D-Link DES-3028 Product Manual - Page 305
Configuration:, its unique Packet Content ACL.
 |
UPC - 790069305375
View all D-Link DES-3028 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 305 highlights
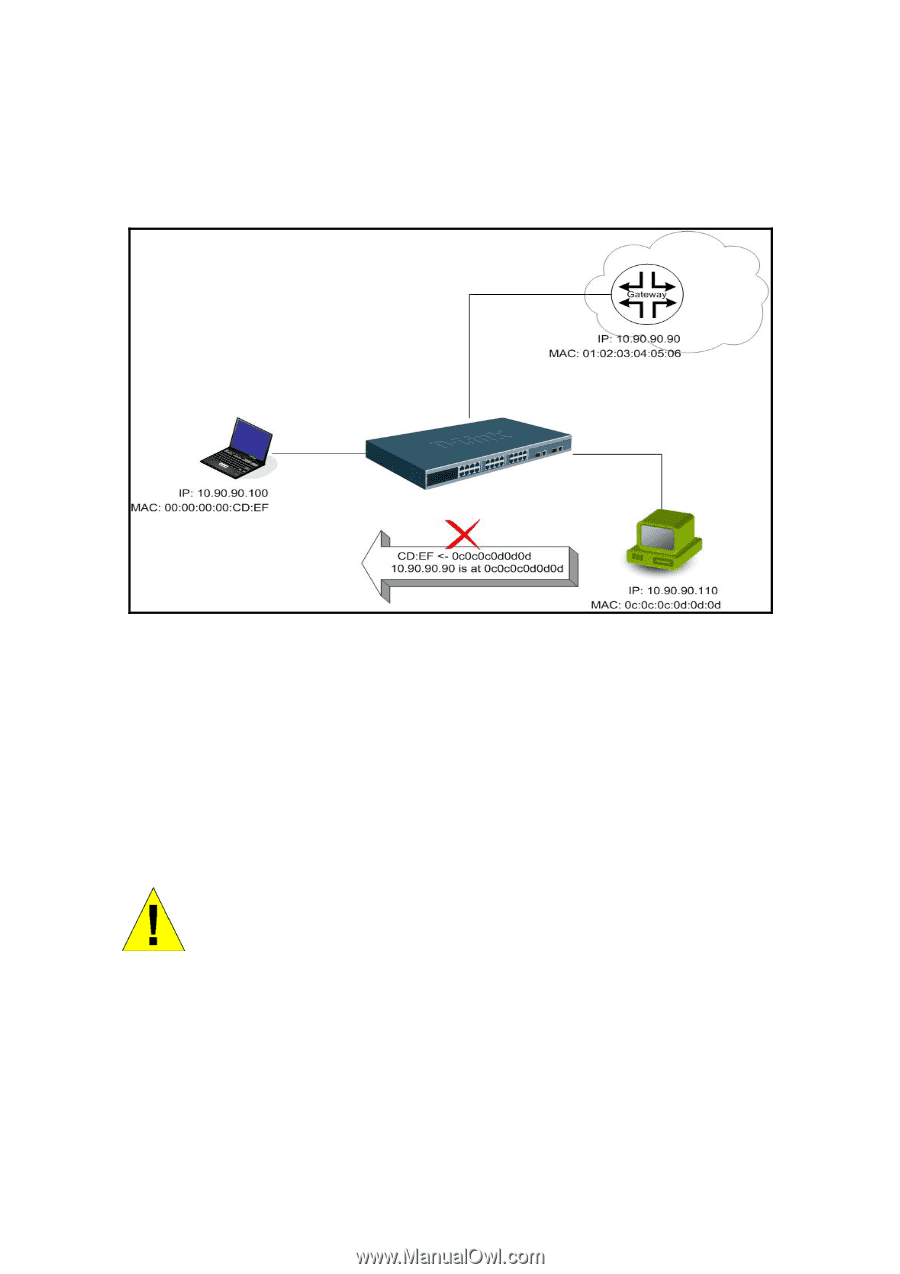
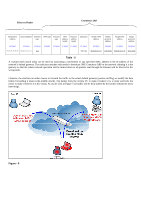
Prevent ARP spoofing via packet content ACL Concerning the common DoS attack today caused by the ARP spoofing, D-Link managed switches can effectively mitigate it via its unique Packet Content ACL. The reason for this is that basic ACLs can only filter ARP packets based on packet type, VLAN ID, Source and Destination MAC information, therefore there is a need for further inspections of ARP packets. To prevent ARP spoofing attacks, we will demonstrate here using the Packet Content ACL on the DES-3028 to block the invalid ARP packets which contain faked gateway's MAC and IP binding. Example Topology Configuration: The design of the Packet Content ACL on the DES-3028 series can inspect any specified content in the first 20 bytes of an ARP packet (up to 80 bytes in total at one time). It utilizes offsets to match individual fields in the Ethernet Frame. An offset contains 16 bytes and the switch supports 5 offsets with each offset being divided into a four 4-byte values in a HEX format. The offset ranges from 0-76. (Refer to the configuration example below for details) In addition, the configuration logics are: 1. Only if the ARP matches the Source MAC addresses in Ethernet, Sender's MAC address and Senders IP address in the ARP protocol can it pass through the switch. (In this example, it is the gateway's ARP.) 2. The switch will deny all other ARP packets which claim they are from the gateway's IP. When calculating packet offset on DES-3028 series, remember that even though a port is an untagged port, the packet will add additional 4 bytes of 802.1Q header (TCI) for switching internal process, shown in Figure-6. All packets will add an additional 4 bytes to assign PVID for the switching internal process.