Cisco 7920 Administration Guide - Page 153
Performing a Site Survey Verification
 |
UPC - 746320774732
View all Cisco 7920 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 153 highlights
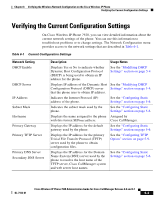
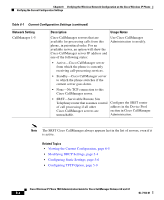
Chapter 6 Verifying the Wireless Network Configuration on the Cisco Wireless IP Phone Performing a Site Survey Verification Table 6-2 802.11b Configuration Network Settings (continued) Network Setting Description References Current User Profile Name of the user profile that the phone is See the "Configuring User currently using. Profiles" section on page 4-29. Current Network Profile Name of the network profile that the phone is currently using. See the "Configuring a Network Profile" section on page 4-18. Key Management Used Type of authentication key management See the "Choosing that the phone is using. Available options Authentication and Encryption include the following: Methods" section on page 2-15. • WPA • CCKM • WPA Pre-shared Key (WPA-PSK) • None Cipher Used Type of cipher used for encryption. Available options include the following: • Unicast: WEP 40, WEP 128, TKIP, None See the "Choosing Authentication and Encryption Methods" section on page 2-15. • Multicast: WEP 40, WEP 128, TKIP, None Related Topics • Verifying Wireless Settings, page 6-6 • Configuring Network Profile Settings, page 5-3 • Configuring Wireless Settings for the Profile, page 5-10 Performing a Site Survey Verification After the initial deployment of wireless phones in the WLAN, it is a good practice to perform site surveys at regular intervals to verify that the APs are providing adequate coverage and that wireless phones can roam from one AP to another with no audio problems. Cisco Wireless IP Phone 7920 Administration Guide for Cisco CallManager Release 4.0 and 4.1 OL-7104-01 6-7