Cisco 5505 Administration Guide - Page 55
or Edit > Add or Edit User Account > VPN Policy > SSL VPN Client > Key Regeneration - support
 |
UPC - 882658082252
View all Cisco 5505 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 55 highlights
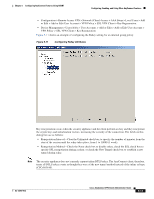
Chapter 5 Configuring AnyConnect Features Using ASDM Configuring, Enabling, and Using Other AnyConnect Features • Configuration > Remote Access VPN > Network (Client) Access > AAA Setup > Local Users > Add or Edit > Add or Edit User Account > VPN Policy > SSL VPN Client > Key Regeneration • Device Management > Users/AAA > User Accounts > Add or Edit > Add or Edit User Account > VPN Policy > SSL VPN Client > Key Regeneration Figure 5-11 shows an example of configuring the Rekey setting for an internal group policy. Figure 5-11 Configuring Rekey Attributes Key renegotiation occurs when the security appliance and the client perform a rekey and they renegotiate the crypto keys and initialization vectors, increasing the security of the connection. The fields on this dialog box are as follows: • Renegotiation Interval-Clear the Unlimited check box to specify the number of minutes from the start of the session until the rekey takes place, from 1 to 10080 (1 week). • Renegotiation Method-Check the None check box to disable rekey, check the SSL check box to specify SSL renegotiation during a rekey, or check the New Tunnel check box to establish a new tunnel during rekey. Note The security appliance does not currently support inline DTLS rekey. The AnyConnect client, therefore, treats all DTLS rekey events as though they were of the new tunnel method instead of the inline ssl type (CSCsh93610). OL-12950-012 Cisco AnyConnect VPN Client Administrator Guide 5-13