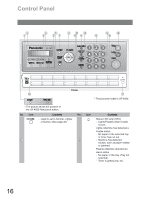
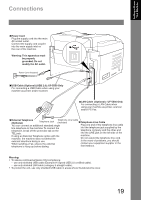
Panasonic UF-4500 Operating Instructions - Page 14
Security Suggestions for Key Operators - key operator id
 |
View all Panasonic UF-4500 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 14 highlights
Security Suggestions for Key Operators To keep your machine's highly-sensitive document data secure, the designated Key Operators are instructed to perform the recommended security measures described below for the initial machine installation, network connection, network configuration, setup of security functions, and replacement and disposal of the machine. 1. Key Operators are required to verify the identity of the manufacturer's service technician, or of an affiliated company's staff, or marketing company, by requesting their ID Card. Do not give the device information by phone or Email. 2. Always connect through a Firewall when installing your device on a network that is connected to the Internet. When connecting this device to a client PC or a server, we recommend configuring your network environment with a switching hub to prevent your device from being wiretapped. 3. A Key Operator ID Code and Passwords is essential to maintaining the security of the device. Key Operators are required to change the ID Code and Passwords from the initial setting, and keep the ID Code and Passwords confidential and in a safe place. 4. To prevent illicit use by unauthorized personnel, perform the following for ID/password settings. 1) Use the maximum number of digits. 2) Use a variety of the accepted character types. 3) Change the ID and password periodically. Make sure that the setting screen can only be seen by the Key Operator when setting/changing various ID and passwords. Keep this information confidential. 5. Delete the data completely before transferring or destroying the device. 6. Scanned(text and images), received and set/ registered information(addresses) are your responsibility. If the device mulfunctions and the data are deleted, it cannot be recovered and is not covered in the warranty. 7. Incorrect settings may leak settings or impede use of this device. Check the details carefully when performing settings. 8. On occasion, the clock may need adjustment. (lunar inequality: 1 minute) The Key Operator plays a critical part in maintaining and controlling the security of the device and in prevention of its unauthorized access, therefore, it is of utmost importance that you understand the content described in the Operating Instructions and that you follow the suggestions herein. 14