ZyXEL P-2602HW-D3A User Guide - Page 231
P-2602HWL-DxA Series User's Guide, VPN Screens, Edit VPN Policies
 |
View all ZyXEL P-2602HW-D3A manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 231 highlights
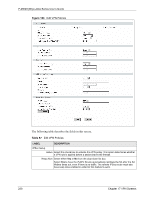
P-2602H(W)(L)-DxA Series User's Guide Table 87 Edit VPN Policies LABEL DESCRIPTION NAT Traversal This function is available if the VPN protocol is ESP. Select this check box if you want to set up a VPN tunnel when there are NAT routers between the ZyXEL Device and remote IPSec router. The remote IPSec router must also enable NAT traversal, and the NAT routers have to forward UDP port 500 packets to the remote IPSec router behind the NAT router. Name Type up to 32 characters to identify this VPN policy. You may use any character, including spaces, but the ZyXEL Device drops trailing spaces. IPSec Key Mode Select IKE or Manual from the drop-down list box. IKE provides more protection so it is generally recommended. Manual is a useful option for troubleshooting if you have problems using IKE key management. Negotiation Mode Select Main or Aggressive from the drop-down list box. Multiple SAs connecting through a secure gateway must have the same negotiation mode. Encapsulation Select Tunnel mode or Transport mode from the drop-down list box. Mode DNS Server (for If there is a private DNS server that services the VPN, type its IP address here. IPSec VPN) The ZyXEL Device assigns this additional DNS server to the ZyXEL Device's DHCP clients that have IP addresses in this IPSec rule's range of local addresses. A DNS server allows clients on the VPN to find other computers and servers on the VPN by their (private) domain names. Local Local IP addresses must be static and correspond to the remote IPSec router's configured remote IP addresses. Two active SAs can have the same configured local or remote IP address, but not both. You can configure multiple SAs between the same local and remote IP addresses, as long as only one is active at any time. In order to have more than one active rule with the Secure Gateway Address field set to 0.0.0.0, the ranges of the local IP addresses cannot overlap between rules. If you configure an active rule with 0.0.0.0 in the Secure Gateway Address field and the LAN's full IP address range as the local IP address, then you cannot configure any other active rules with the Secure Gateway Address field set to 0.0.0.0. Local Address Use the drop-down menu to choose Single, Range, or Subnet. Select Single for Type a single IP address. Select Range for a specific range of IP addresses. Select Subnet to specify IP addresses on a network by their subnet mask. IP Address Start When the Local Address Type field is configured to Single, enter a (static) IP address on the LAN behind your ZyXEL Device. When the Local Address Type field is configured to Range, enter the beginning (static) IP address, in a range of computers on your LAN behind your ZyXEL Device. When the Local Address Type field is configured to Subnet, this is a (static) IP address on the LAN behind your ZyXEL Device. End / Subnet Mask When the Local Address Type field is configured to Single, this field is N/A. When the Local Address Type field is configured to Range, enter the end (static) IP address, in a range of computers on the LAN behind your ZyXEL Device. When the Local Address Type field is configured to Subnet, this is a subnet mask on the LAN behind your ZyXEL Device. Chapter 17 VPN Screens 231