Cisco 6941 Administration Guide - Page 28
Overview of Supported Security Features, Topic, Reference, Feature, Description - firmware
 |
UPC - 882658277801
View all Cisco 6941 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 28 highlights
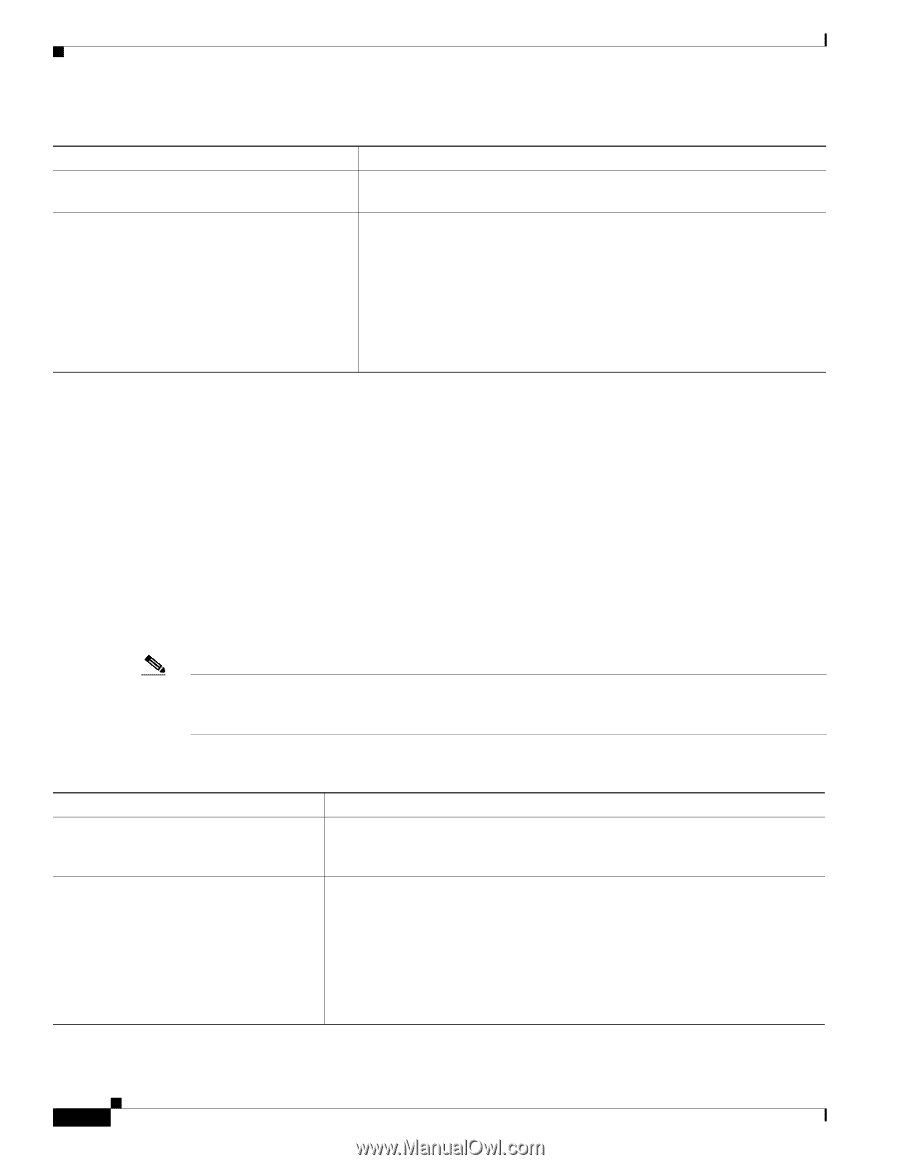
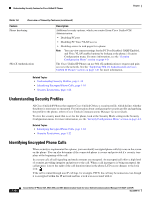
Understanding Security Features for Cisco Unified IP Phones Chapter Table 1-5 Cisco Unified IP Phone and Cisco Unified CM Security Topics (continued) Topic Resetting or restoring the phone 802.1X Authentication for Cisco Unified IP Phones Reference See the "Resetting or Restoring the Cisco Unified IP Phone" section on page 9-12 See these sections: • "Supporting 802.1X Authentication on Cisco Unified IP Phones" section on page 1-21 • "Security Configuration Menu" section on page 4-9 • "Status Menu" section on page 7-2 • "Troubleshooting Cisco Unified IP Phone Security" section on page 9-8 All Cisco Unified IP Phones that support Cisco Unified CM use a security profile, which defines whether the phone is nonsecure or secure. For information about configuring the security profile and applying the profile to the phone, refer to Cisco Unified Communications Manager Security Guide. Overview of Supported Security Features Table 1-6 provides an overview of the security features that the Cisco Unified IP Phone 6921, 6941, and 6961 support. For more information about these features and about Cisco Unified CM and Cisco Unified IP Phone security, refer to Cisco Unified Communications Manager Security Guide. For information about current security settings on a phone, choose Applications > Admin Settings > Security Setup. For more information, see the "Security Configuration Menu" section on page 4-9. Note Most security features are available only if a certificate trust list (CTL) is installed on the phone. For more information about the CTL, refer to "Configuring the Cisco CTL Client" chapter in Cisco Unified Communications Manager Security Guide. Table 1-6 Overview of Security Features Feature Image authentication Customer-site certificate installation Description Signed binary files (with the extension .sgn) prevent tampering with the firmware image before it is loaded on a phone. Tampering with the image causes a phone to fail the authentication process and reject the new image. Each Cisco Unified IP Phone requires a unique certificate for device authentication. Phones include a manufacturing installed certificate (MIC), but for additional security, you can specify in Cisco Unified CM Administration that a certificate be installed by using the Certificate Authority Proxy Function (CAPF). Alternatively, you can install a Locally Significant Certificate (LSC) from the Security Configuration menu on the phone. See the "Configuring Security on the Cisco Unified IP Phone" section on page 3-16 for more information. 1-16 Cisco Unified IP Phone 6921, 6941, 6945, and 6961 Administration Guide for Cisco Unified Communications Manager 8.5 (SCCP and SIP) OL-23769-01