HP Integrity rx2800 HP Smart Update Manager User Guide - Page 103
Recovering from a blocked program on Microsoft Windows, Configuring Windows firewall settings
 |
View all HP Integrity rx2800 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 103 highlights
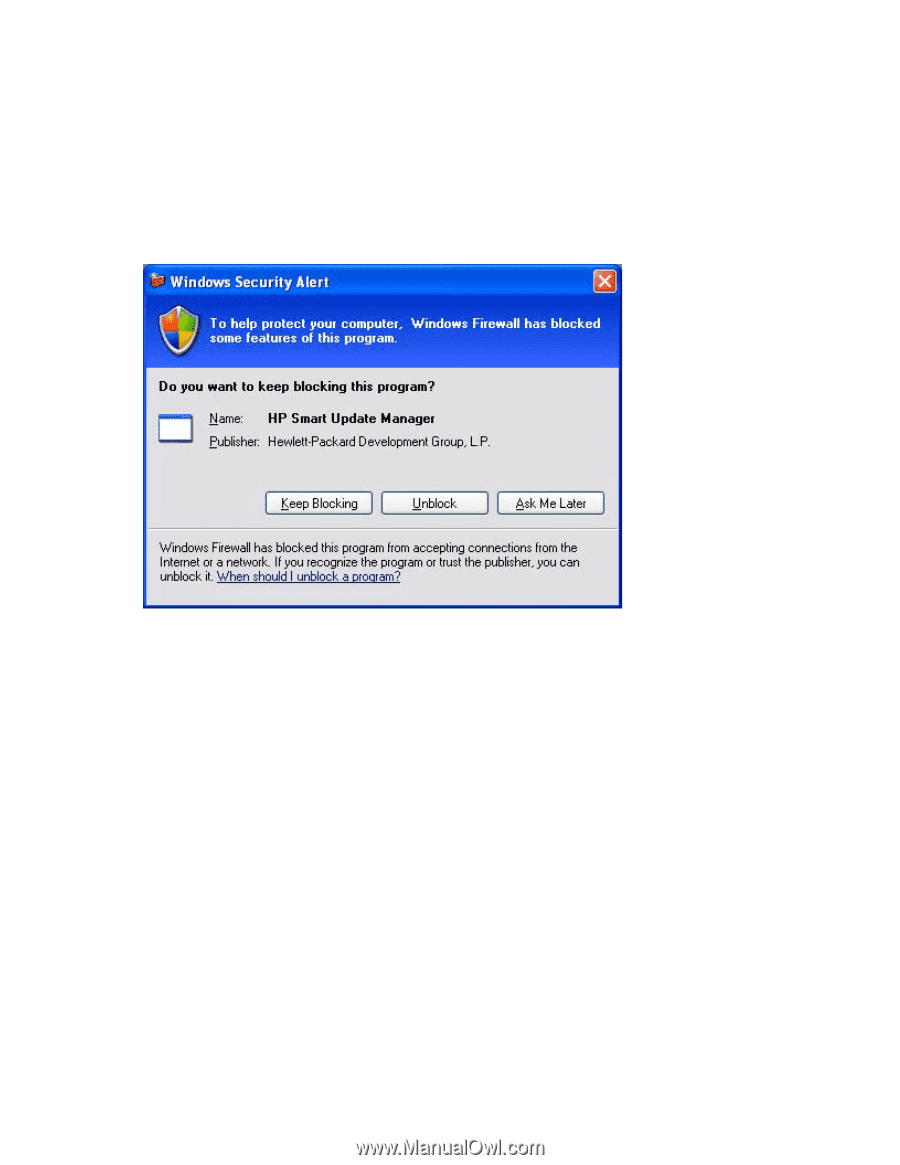
Recovering from a blocked program on Microsoft Windows Configuring Windows firewall settings The Windows® Security Alert appears when a program is blocked from accepting connections from the Internet or a network. To set the rules for the Windows® Firewall and Security Policy, click Unblock, and then set your firewall settings to the following: 1. Click Start>Control Panel>Administrative Tools>Windows Firewall with Advanced Security>Inbound Rules>Remote Administration (NP-IN). 2. Select Enabled, and then select Allow the connections. For Direct to iLO support, you must enable ping. Enabling ports in HP Smart Update Manager The ports that HP Smart Update Manager uses cannot be configured. When HP Smart Update Manager port initiates communications to remote targets, it uses several well-known ports depending on the operating system. For Windows®, it uses ports 138 and 445 to connect to remote targets (equivalent to remote and file print share functionality). For Linux, HP Smart Update Manager uses port 22 (SSH) to start the communications with the remote target. HP Smart Update Manager uses defined ports to communicate between the remote target and the workstation where HP Smart Update Manager is executing. When you run HP Smart Update Manager, it uses the administrator/root privileges to dynamically register the port with the default Windows® and Linux firewalls for the length of the application execution, then closes and deregisters the port. All communications are over a SOAP server using SSL with additional functionality to prevent man-in-themiddle, packet spoofing, packet replay, and other attacks. The randomness of the port helps prevent port Troubleshooting 103