HP rp3440 HP Integrity and HP 9000 iLO MP Operations Guide, Fifth Edition - Page 121
IP Address Range Restrictions, IP Address and Subnet Mask Restrictions, DNS-Based Restrictions
 |
View all HP rp3440 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 121 highlights
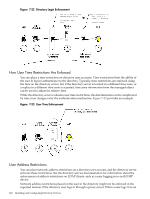
MP firmware can cause the iLO MP device clock not to be set. Also, the host time must be correct for the iLO MP device to preserve time across firmware flashes. IP Address Range Restrictions IP address range restrictions enable you to specify network addresses that are granted or denied access by the restriction. The address range is typically specified in a low-to-high range format. You can specify an address range to grant or deny access to a single address. Addresses that fall within the low-to-high IP address range meet the IP address restriction. IP Address and Subnet Mask Restrictions IP address and subnet mask restrictions enable you to specify a range of addresses that are granted or denied access by the restriction. This format has similar capabilities to those in an IP address range but can be more native to your networking environment. An IP address and subnet mask range is typically specified using a subnet address and address bit mask that identifies addresses on the same logical network. In binary math, if the bits of a client machine address are added to the bits of the subnet mask and these bits match the restriction subnet address, the client machine meets the restriction. DNS-Based Restrictions DNS-based restrictions use the network naming service to examine the logical name of the client machine by looking up machine names assigned to the client IP addresses. DNS restrictions require a functional name server. If the name service fails or cannot be reached, DNS restrictions cannot be matched and will fail. DNS-based restrictions can limit access to a single, specific machine name or to machines sharing a common domain suffix. For example, the DNS restriction www.hp.com matches hosts that are assigned the domain name www.hp.com. However, the DNS restriction *.hp.com matches any machine originating from HP. DNS restrictions can cause some ambiguity because a host can be multi-homed. DNS restrictions do not necessarily match one-to-one with a single system. Using DNS-based restrictions can create some security complications. Name service protocols are insecure. Any individual with malicious intent and access to the network can place a rogue DNS service on the network, creating fake address restriction criteria. Organizational security policies should be taken into consideration when implementing DNS-based address restrictions. Role Address Restrictions Role address restrictions are enforced by the iLO MP firmware, based on the client's IP network address. When the address restrictions are met for a role, the rights granted by the role apply. Address restrictions can be difficult to manage if access is attempted across firewalls or through network proxies. Either of these mechanisms can change the apparent network address of the client, causing the address restrictions to be enforced in an unexpected manner. How Directory Login Restrictions Are Enforced Figure 7-22 shows how two sets of restrictions potentially limit a directory user's access to iLO MP devices. User access restrictions limit a user's access to authenticate to the directory. Role access restrictions limit an authenticated user's ability to receive iLO MP privileges based on rights specified in one or more roles. Directory-Enabled Management 121