HP rp3440 HP Integrity and HP 9000 iLO MP Operations Guide, Fifth Edition - Page 123
Creating Multiple Restrictions and Roles, Multiple Restriction Roles
 |
View all HP rp3440 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 123 highlights
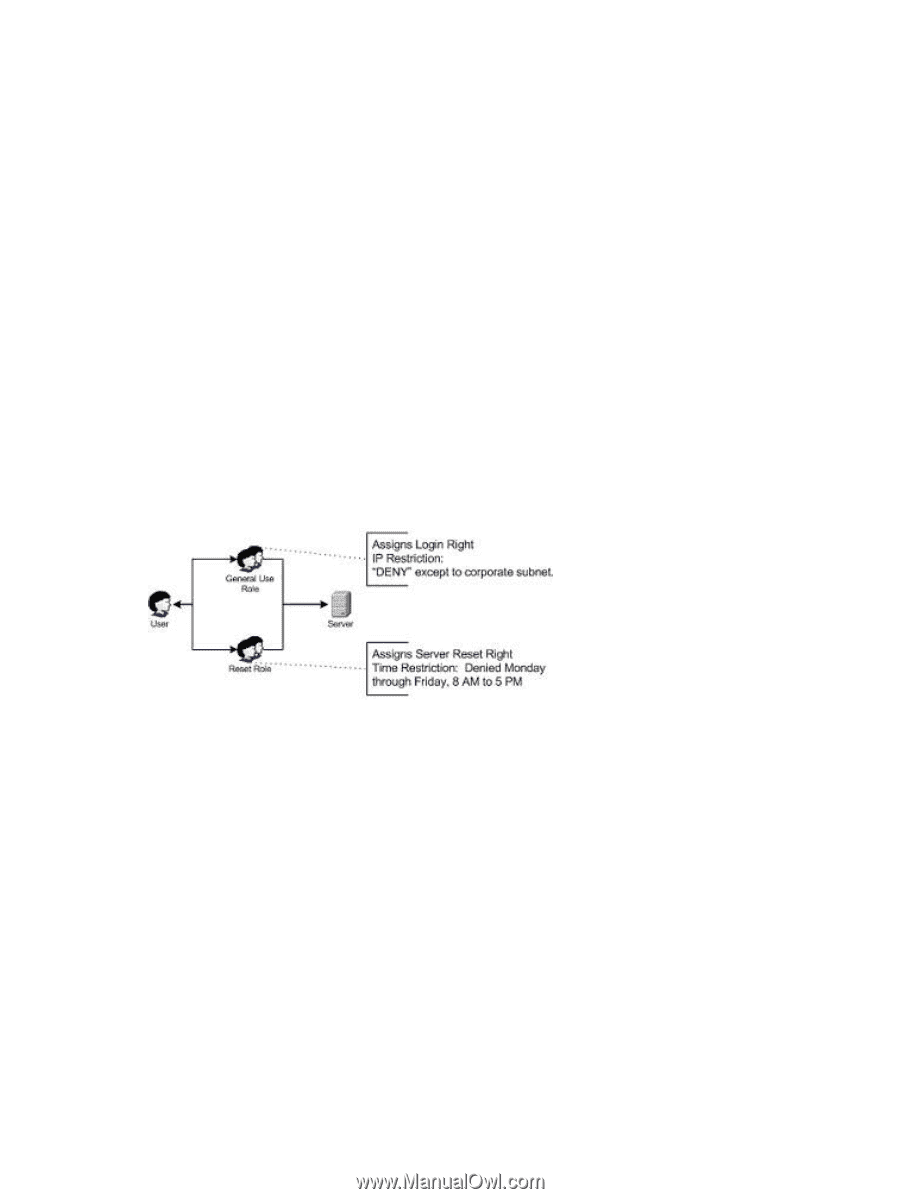
iLO MP device as a directory user, the iLO MP device attempts authentication to the directory as that user, which means that address restrictions placed on the user account apply when accessing the iLO MP device. However, because the user is proxied at the iLO MP device, the network address of the authentication attempt is that of the iLO MP device, not that of the client workstation. Creating Multiple Restrictions and Roles The most useful application of multiple roles includes restricting one or more roles so that rights do not apply in all situations. Other roles provide different rights under different constraints. Using multiple restrictions and roles enables you to create arbitrary, complex rights relationships with a minimum number of roles. For example, an organization might have a security policy in which iLO MP administrators are allowed to use the iLO MP device from within the corporate network, but are only able to reset the server outside of regular business hours. Directory administrators might be tempted to create two roles to address this situation, but extra caution is required. Creating a role that provides the required server reset rights and restricting it to an after-hours application might allow administrators outside the corporate network to reset the server, which is contrary to most security policies. In Figure 7-24, security policy dictates that general use is restricted to clients within the corporate subnet, and server reset capability is additionally restricted to after hours. Figure 7-24 Multiple Restriction Roles Alternatively, the directory administrator could create a role that grants the login right and restrict it to the corporate network and create another role that grants only the server reset right and restrict it to after-hours operation. This configuration is easier to manage but more dangerous because ongoing administration can create another role that grants users from addresses outside the corporate network the login right, which could unintentionally grant the iLO MP administrators in the server Reset role the ability to reset the server from anywhere, provided they satisfy the time constraints of that role. The previous configuration satisfies corporate security policy. However, adding another role that grants the login right can inadvertently grant server reset privileges from outside the corporate subnet after hours. Figure 7-25 shows a more manageable solution that restricts the Reset role, as well as the General Use role. Directory-Enabled Management 123