McAfee DTP-1650-MGRA Installation Guide - Page 37
MTA requirements for McAfee DLP Prevent, McAfee Email Security Appliance
 |
View all McAfee DTP-1650-MGRA manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 37 highlights
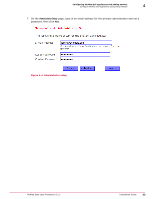
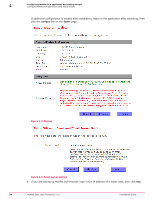
Configuring McAfee DLP appliances and adding servers Configuring McAfee DLP Prevent 4 McAfee DLP Prevent can be configured with many different email and webmail systems. McAfee Email and Web Gateway products are supported, and it has also been tested with some third party systems, such as Blue Coat Systems products. McAfee Email Security Appliance is set to handle up to 30 concurrent SMTP connections ‑ but McAfee DLP Prevent exceeds this limit. To get these two appliances to work together, you must modify the ESA configuration files. MTA requirements for McAfee DLP Prevent Before setting up McAfee DLP Prevent, you must determine if your MTA (message transfer agent) can support interoperability. Before installing McAfee DLP Prevent, make sure that your email gateway has all of the following capabilities. • By incoming and outgoing, we mean emails that are either being sent to or received from the outside world. • By entering and leaving, we mean emails that are entering or leaving the MTA. 1 Must be capable of sending either all or a portion of outgoing traffic to the McAfee DLP Prevent application. McAfee DLP Prevent is not typically used to inspect incoming email. Examples of a requirement where only a portion of the traffic needs to be scanned might be in environments where only traffic with attachments is to be scanned, or where scanning is limited to traffic directed to public sites (for example, Yahoo). 2 Must be capable of inspecting email headers of messages entering the MTA. 3 Must be capable of taking actions based on specified match expressions for email headers. The specific header strings received from McAfee DLP Prevent are the X header X‑RCIS‑Action header with values ALLOW, BLOCK, QUART, ENCRYPT, BOUNCE, REDIR and NOTIFY. 4 Based on entering port or some other metric, must be capable of distinguishing between all emails arriving from the McAfee DLP Prevent appliance, then applying header inspection and header‑based action rules exclusively to incoming email from McAfee DLP Prevent. 5 Must be capable of ensuring that emails arriving from the McAfee DLP Prevent appliance are not routed back to the McAfee DLP Prevent appliance. This can be done either by using port / srcIP‑based mail routing, checking to see if an X‑RCIS‑Action header already exists in an email scheduled to be routed to the McAfee DLP Prevent appliance, or by some other means. 6 Must be capable of implementing all of the McAfee DLP Prevent‑based actions. If the MTA does not have all of the required capabilities, inter‑operation is still possible - but in that case, the actions that can be set when rules are created must be limited to those supported by the MTA. 7 Must be able to inter‑operate with an email encryption appliance (if this capability is needed) and instruct the encryption appliance to encrypt specific messages based on header information or other metrics. McAfee Data Loss Prevention 9.2.1 Installation Guide 37