Netgear WNDAP660 Reference Manual - Page 91
Table 24., IDS/IPS policies and policy rules continued, Attack, Result, Detection, Solution, Policy
 |
View all Netgear WNDAP660 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 91 highlights
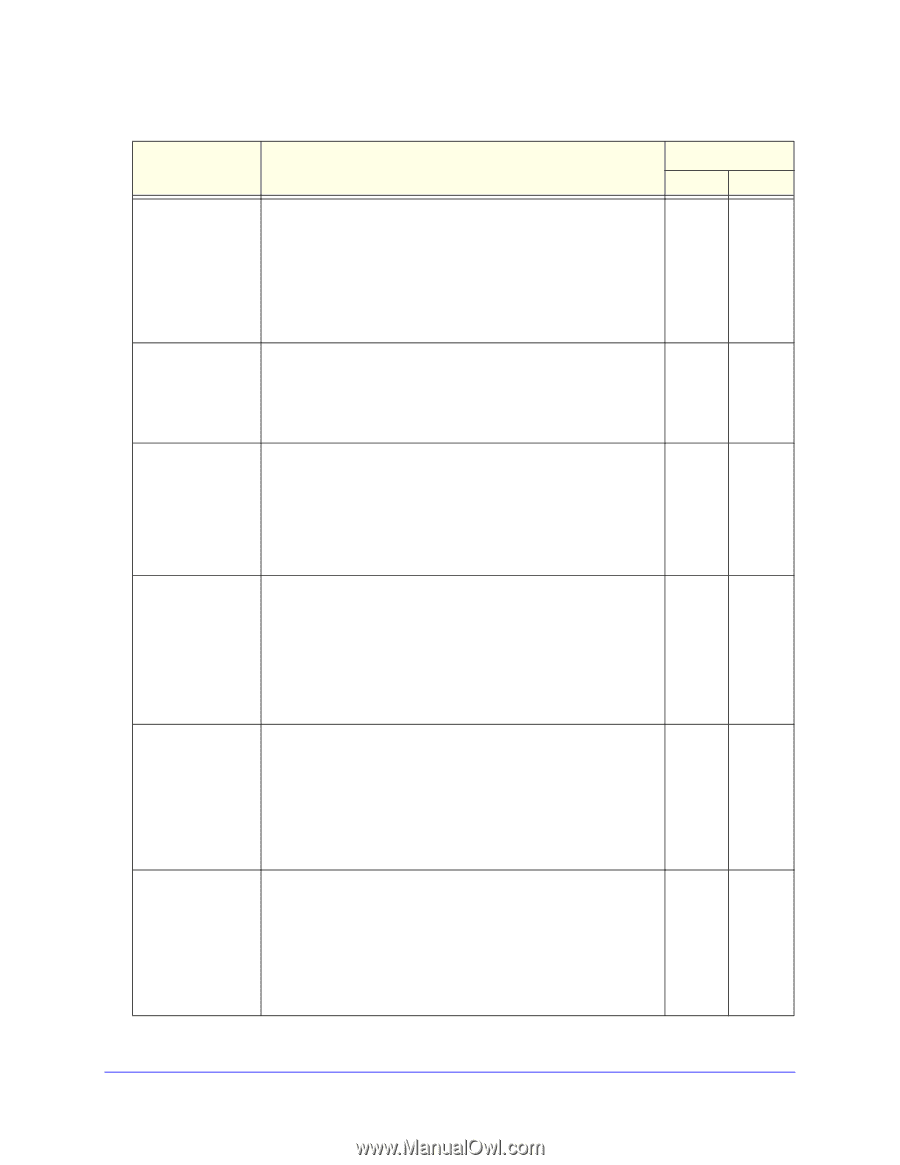
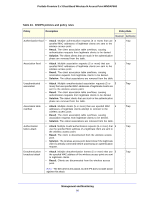
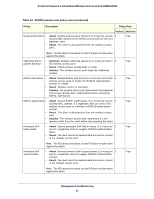
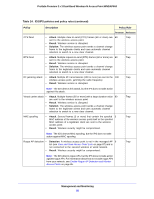
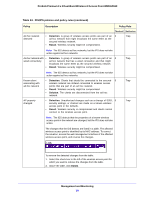
ProSafe Premium 3 x 3 Dual-Band Wireless-N Access Point WNDAP660 Table 24. IDS/IPS policies and policy rules (continued) Policy Description Policy Rule Threshold Notification Disassociation flood • • Attack. Multiple disassociation frames (5 or more) that use the 5 spoofed MAC address of the wireless access point are sent to a legitimate client. Result. The client is disconnected from the wireless access point. Trap Note: The IDS detects this attack, but the IPS does not take action against this attack. Malformed 802.11 packets detected • Detection. Multiple malformed packets (5 or more) are sent to 5 the wireless access point. • Result. Clients behave unexpectedly or crash. • Solution. The wireless access point drops the malformed packets. EAPOL-start attack • Attack. Multiple EAPOL start frames (5 or more) are sent to the 5 wireless access point to initiate the RADIUS authentication process for clients. • Result. Wireless service is disrupted. • Solution. The wireless access point determines if the legitimate clients have already been authenticated before processing EAPOL start frames. EAPOL-logoff attack • • • Attack. Several EAPOL logoff frames (2 or more) that use the 2 spoofed MAC address of a legitimate client are sent to the wireless access point to terminate a RADIUS-authenticated session. Result. The client is disconnected from the wireless access point. Solution. The wireless access point determines if it still receives traffic from the client before disconnecting the client. Premature EAP failure attack • Attack. Several premature EAP failure frames (2 or more) are 2 sent to a legitimate client to suggest RADIUS authentication failure. • Result. The client cannot be authenticated and cannot connect to the wireless access point. Trap Trap Trap Trap Premature EAP success attack Note: The IDS detects this attack, but the IPS does not take action against this attack. • Attack. Several premature EAP success frames (2 or more) are 2 sent to a legitimate client to suggest RADIUS authentication success. • Result. The client cannot be authenticated and cannot connect to the wireless access point. Trap Note: The IDS detects this attack, but the IPS does not take action against this attack. Management and Monitoring 91