TP-Link EAP245 EAP Controller V2.4.7 User Guide - Page 27
View Past Guest Authorization, 2.8 View Logs
 |
View all TP-Link EAP245 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 27 highlights
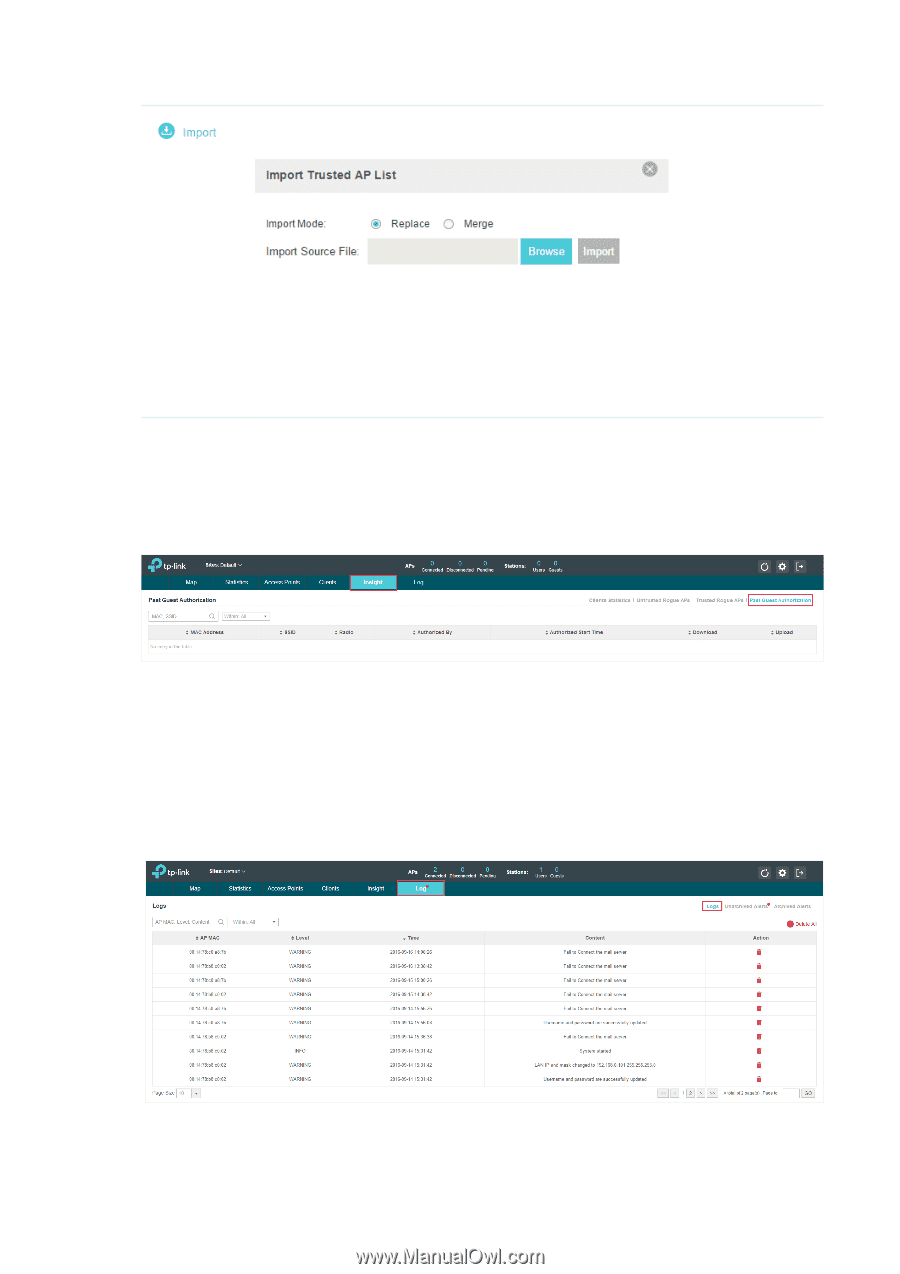
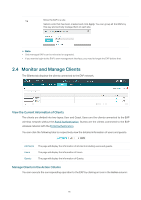
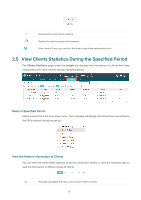
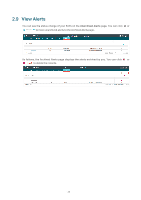
Import a saved Trusted Rogue APs list. If the MAC address of an AP appears in list, it will not be detected as a rogue AP. Please follow the steps below: 1. Select Replace (replace the current Trusted Rogue APs list with the one you import) or Merge (add the APs in the file to the current Trusted Rogue APs list). 2. Click Browse to locate the file and choose it. 3. Click Import to import the Trusted Rogue APs list. 2.7 View Past Guest Authorization The Past Guest Authorization page displays the details about all the clients that accessed the network during a certain time period. You can select a period in the drop-down list. 2.8 View Logs The logs of the EAP Controller can effectively record, classify and manage the system information of the managed EAPs, providing powerful support for network administrator to monitor network operation and diagnose malfunctions. The Logs page displays EAP's MAC address, level, occurred time and content. 22