TP-Link T2500-28TCTL-SL5428E T2500-28TCUN V1 CLI Reference Guide - Page 19
PPPoE Circuit-ID Insertion Commands, IP Verify Source Commands
 |
View all TP-Link T2500-28TCTL-SL5428E manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 19 highlights
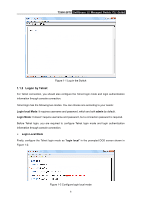
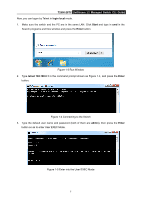
T2500-28TC JetStream L2 Managed Switch CLI Guide Provide information about the commands used for configuring GVRP (GARP VLAN registration protocol). Chapter 10: EtherChannel Commands Provide information about the commands used for configuring LAG (Link Aggregation Group) and LACP (Link Aggregation Control Protocol). Chapter 11: User Manage Commands Provide information about the commands used for user management. Chapter 12: Binding Table Commands Provide information about the commands used for binding the IP address, MAC address, VLAN and the connected Port number of the Host together. Besides it also provide information about the commands used for monitoring the process of the Host obtaining the IP address from DHCP server, and record the IP address, MAC address, VLAN and the connected Port number of the Host for automatic binding. Chapter 13: ARP Inspection Commands Provide information about the commands used for protecting the switch from the ARP cheating or ARP Attack. Chapter 14: IP Verify Source Commands Provide information about the commands used for guarding the IP Source by filtering the IP packets based on the IP-MAC Binding entries. Chapter 15: DoS Defend Command Provide information about the commands used for DoS defend and detecting the DoS attack. Chapter 16: IEEE 802.1X Commands Provide information about the commands used for configuring IEEE 802.1X function. Chapter 17: PPPoE Circuit-ID Insertion Commands Provide information about the commands used for configuring PPPoE Circuit-ID function. Chapter 18: System Log Commands Provide information about the commands used for configuring system log. Chapter 19: SSH Commands Provide information about the commands used for configuring and managing SSH (Security Shell). Chapter 20: SSL Commands Provide information about the commands used for configuring and managing SSL (Secure Sockets Layer). Chapter 21: MAC Address Commands 2