ZyXEL GS1500-24P User Guide - Page 132
ARP Table Entries, How Dynamic ARP Works, ARP Inspection Overview
 |
View all ZyXEL GS1500-24P manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 132 highlights
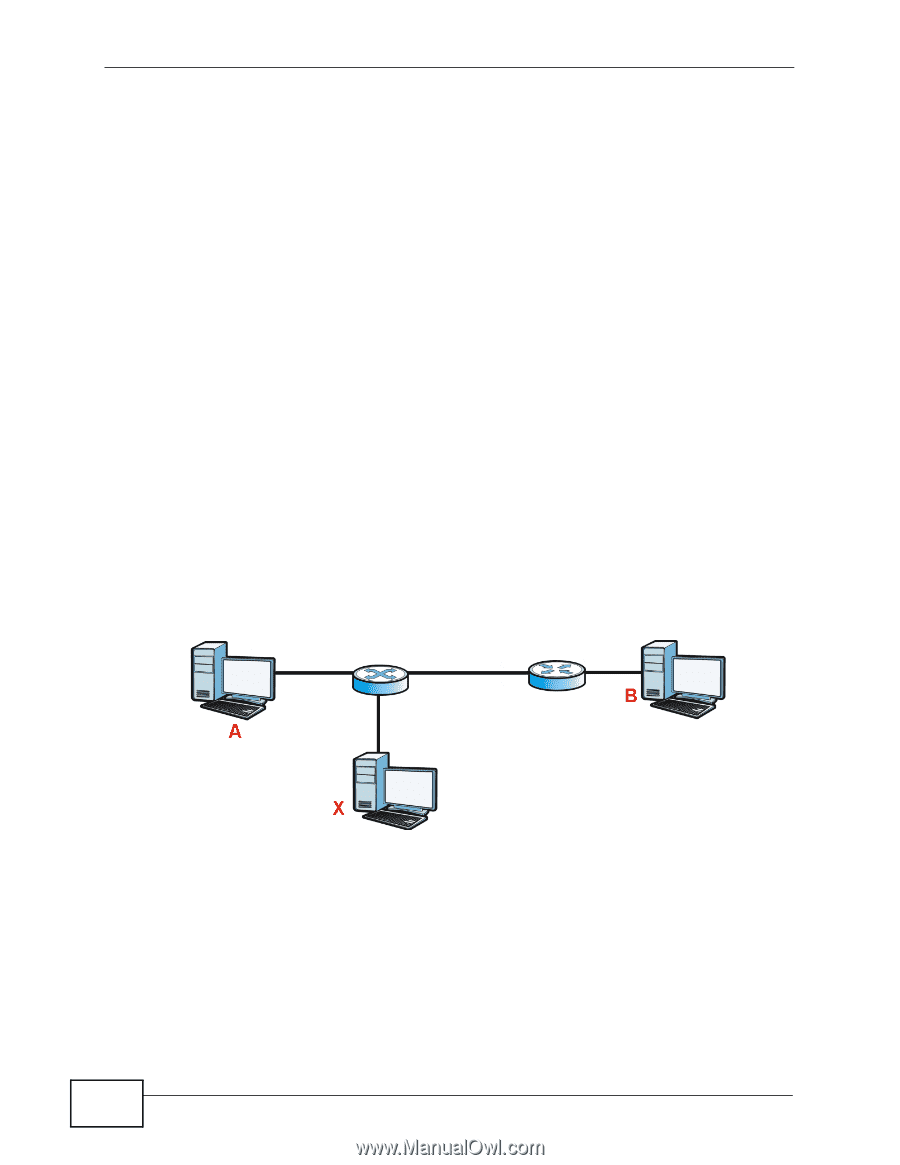
Chapter 18 Dynamic ARP 18.3.1 ARP Table Entries The ARP table is populated with MAC and corresponding IP address mappings in two different ways. • DHCP Snooping - The Switch listens to traffic from a DHCP server on a trusted port and learns IP-to-MAC address bindings by parsing DHCP ACK packets. • Static Entries - The Switch administrator can enter static IP-to-MAC address mappings via the web configurator. 18.3.2 How Dynamic ARP Works When an incoming ARP packet destined for a host device on a local area network arrives at the Switch, the Switch's ARP program looks in the ARP table and, if it finds the address, sends it to the device. If no entry is found for the IP address, dynamic ARP discards the ARP packet. 18.3.3 ARP Inspection Overview Use ARP inspection to filter unauthorized ARP packets on the network. This can prevent many kinds of man-in-the-middle attacks, such as the one in the following example. Figure 63 Example: Man-in-the-middle Attack 132 In this example, computer B tries to establish a connection with computer A. Computer X is in the same broadcast domain as computer A and intercepts the ARP request for computer A. Then, computer X does the following things: • It pretends to be computer A and responds to computer B. • It pretends to be computer B and sends a message to computer A. As a result, all the communication between computer A and computer B passes through computer X. Computer X can read and alter the information passed between them. GS1500-24P User's Guide