D-Link DIS-200G Emulator - Page 105
DoS Attack Prevention Settings, TCP SYN SrcPort Less 1024
 |
View all D-Link DIS-200G manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 105 highlights
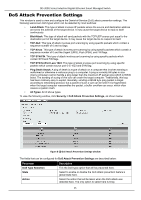
DIS-200G Series Industrial Gigabit Ethernet Smart Managed Switch DoS Attack Prevention Settings This window is used to view and configure the Denial-of-Service (DoS) attack prevention settings. The following well-known DoS types which can be detected by most switches: • Land Attack: This type of attack involves IP packets where the source and destination address are set to the address of the target device. It may cause the target device to reply to itself continuously. • Blat Attack: This type of attack will send packets with the TCP/UDP source port equal to the destination port of the target device. It may cause the target device to respond to itself. • TCP-Null: This type of attack involves port scanning by using specific packets which contain a sequence number of 0 and no flags. • TCP-Xmas: This type of attack involves port scanning by using specific packets which contain a sequence number of 0 and the Urgent (URG), Push (PSH), and FIN flags. • TCP SYN-FIN: This type of attack involves port scanning by using specific packets which contain SYN and FIN flags. • TCP SYN SrcPort Less 1024: This type of attack involves port scanning by using specific packets which contain source port 0 to 1023 and SYN flag. • Ping Death Attack: A ping of death is a type of attack on a computer that involves sending a malformed or otherwise a malicious ping to a computer. A ping is normally 64 bytes in size (many computers cannot handle a ping larger than the maximum IP packet size) which is 65535 bytes. The sending of a ping of this size can crash the target computer. Traditionally, this bug has been relatively easy to exploit. Generally, sending a 65536 byte ping packet is illegal according to networking protocol, but a packet of such a size can be sent if it is fragmented; when the target computer reassembles the packet, a buffer overflow can occur, which often causes a system crash. • All Types: All of above types. To view the following window, click Security > DoS Attack Prevention Settings, as shown below: Figure 8-10 DoS Attack Prevention Settings window The fields that can be configured for DoS Attack Prevention Settings are described below: Parameter DoS Type Selection State Action Description Tick the DoS type option that will be prevented here. Select to enable or disable the DoS attack prevention feature's global state here. Select the action that will be taken when the DoS attack was detected here. The only option to select here is Drop. 95