Netgear DG834G DG834Gv5 Reference Manual - Page 31
Wireless Security Options, WPA-802.1x, WPA-PSK TKIP, WPA2-PSK AES - maximum wireless connections
 |
UPC - 606449029918
View all Netgear DG834G manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 31 highlights
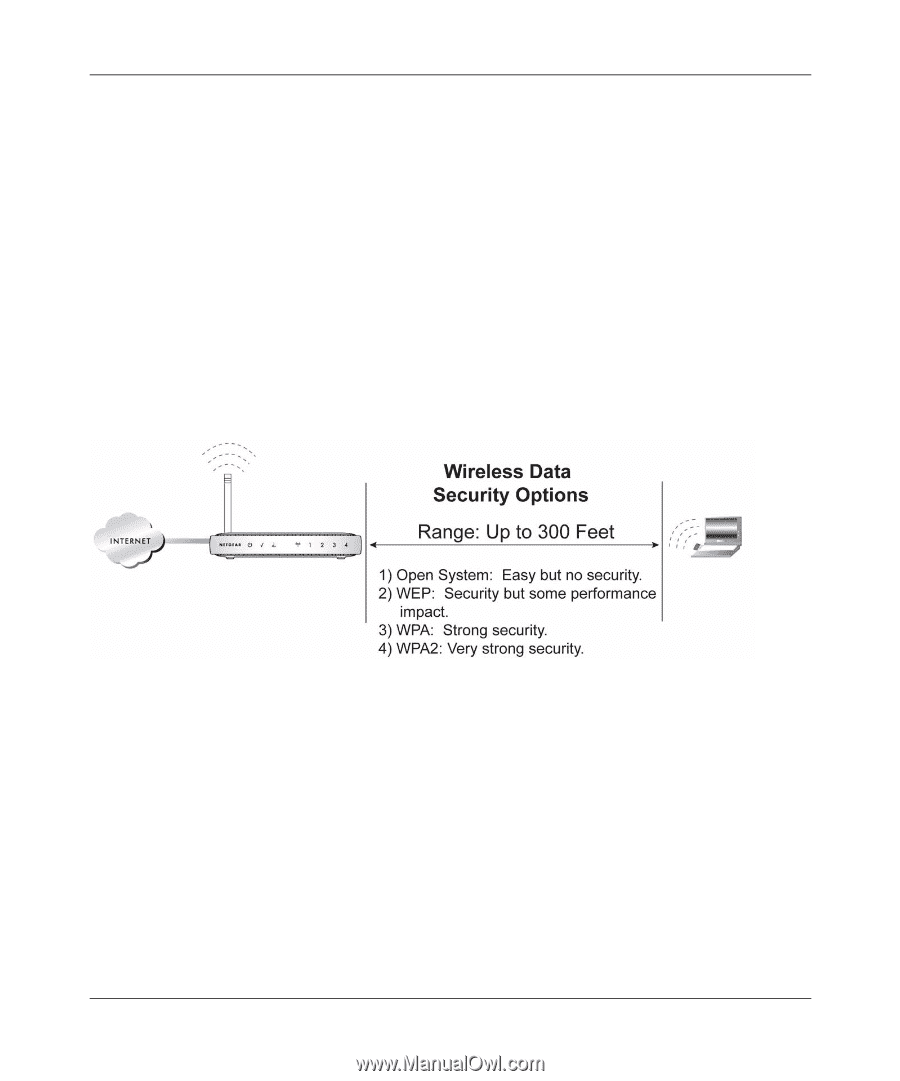
Wireless ADSL2+ Modem Router DG834G User Manual The time it takes to establish a wireless connection can vary depending on both your security settings and placement. WEP connections can take slightly longer to establish. Also, WEP encryption can consume more battery power on a notebook computer. Wireless Security Options Indoors, computers can connect over 802.11g wireless networks at a maximum range of up to 300 feet. Such distances can allow for others outside your immediate area to access your network. Unlike wired network data, your wireless data transmissions can extend beyond your walls and can be received by anyone with a compatible adapter. For this reason, use the security features of your wireless equipment. The ADSL2+ Modem Wireless Router provides highly effective security features which are covered in detail in this chapter. Deploy the security features appropriate to your needs. There are several ways you can enhance the security of your wireless network: Figure 2-1 • WEP. Wired Equivalent Privacy (WEP) data encryption provides data security. WEP Shared Key authentication and WEP data encryption block all but the most determined eavesdropper. This data encryption mode has been superseded by WPA-PSK and WPA2-PSK (see "Configuring WEP" on page 2-4).. • WPA-802.1x, WPA2-802.1x. Wi-Fi Protected Access (WPA) with user authentication implemented using IEE 802.1x and RADIUS servers. • WPA-PSK (TKIP), WPA2-PSK (AES). Wi-Fi Protected Access (WPA) using a pre-shared key to perform authentication and generate the initial data encryption keys. The very strong authentication along with dynamic per frame re-keying of WPA makes it virtually impossible to compromise"Configuring WPA, WPA2, or WPA/WPA2" on page 2-6). Configuring Your Wireless Network and Security Settings 2-3 v1.0, May 2008