Netgear DG834G DG834Gv5 Reference Manual - Page 97
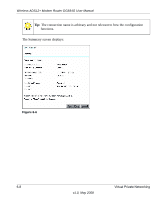
Planning a VPN, Table 6-1., VPN Tunnel Configuration Worksheet
 |
UPC - 606449029918
View all Netgear DG834G manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 97 highlights
Planning a VPN Wireless ADSL2+ Modem Router DG834G User Manual When you set up a VPN, it is helpful to plan the network configuration and record the configuration parameters on a worksheet: Table 6-1. VPN Tunnel Configuration Worksheet Connection Name: Pre-Shared Key: Secure Association -- Main Mode or Manual Keys: Perfect Forward Secrecy -- Enabled or Disabled: Encryption Protocol -- DES or 3DES: Authentication Protocol -- MD5 or SHA-1: Diffie-Hellman (DH) Group -- Group 1 or Group 2: Key Life in seconds: IKE Life Time in seconds: VPN Endpoint Local IPSec ID LAN IP Address Subnet Mask FQDN or Gateway IP (WAN IP Address) To set up a VPN connection, you must configure each endpoint with specific identification and connection information describing the other endpoint. You must configure the outbound VPN settings on one end to match the inbound VPN settings on other end, and vice versa. This set of configuration information defines a security association (SA) between the two VPN endpoints. When planning your VPN, you must make a few choices first: • Will the local end be any device on the LAN, a portion of the local network (as defined by a subnet or by a range of IP addresses), or a single PC? • Will the remote end be any device on the remote LAN, a portion of the remote network (as defined by a subnet or by a range of IP addresses), or a single PC? Virtual Private Networking 6-3 v1.0, May 2008