Netgear WNHDE111 WNHDE111 User Manual - Page 39
Table 4-1., Wireless Security Options, Other Features That Enhance Security - troubleshooting
 |
UPC - 606449054279
View all Netgear WNHDE111 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 39 highlights
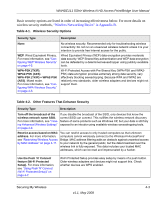
WNHDE111 5GHz Wireless-N HD Access Point/Bridge User Manual Basic security options are listed in order of increasing effectiveness below. For more details on wireless security methods, "Wireless Networking Basics" in Appendix B. Table 4-1. Wireless Security Options Security Type Description None. WEP. Wired Equivalent Privacy. For more information, see "Configuring WEP Wireless Security" on page 4-5. WPA-PSK (TKIP). WPA2-PSK (AES). WPA-PSK (TKIP) + WPA2-PSK (AES). Mixed mode. For more information, see "Configuring WPA Wireless Security" on page 4-6. No wireless security. Recommended only for troubleshooting wireless connectivity. Do not run an unsecured wireless network unless it is your intention to provide free Internet access for the public. Wired Equivalent Privacy (WEP) data encryption provides moderate data security. WEP Shared Key authentication and WEP data encryption can be defeated by a determined eavesdropper using publicly available tools. Wi-Fi Protected Access with Pre-Shared Key (WPA-PSK and WPA2PSK) data encryption provides extremely strong data security, very effectively blocking eavesdropping. Because WPA and WPA2 are relatively new standards, older wireless adapters and devices might not support them. Table 4-2. Other Features That Enhance Security Security Type Description Turn off the broadcast of the If you disable the broadcast of the SSID, only devices that know the wireless network name SSID. correct SSID can connect. This nullifies the wireless network discovery For more information, see "View- feature of some products such as Windows XP, but your data is still fully ing Advanced Wireless Settings" exposed to an intruder using available wireless eavesdropping tools. on page 4-6. Restrict access based on MAC address. For more information, see "Restricting Wireless Access by MAC Address" on page 4-11. You can restrict access to only trusted computers so that unknown computers cannot wirelessly connect to the Wireless-N AccessPoint/ Bridge. MAC address filtering adds an obstacle against unwanted access to your network by the general public, but the data broadcast over the wireless link is fully exposed. This data includes your trusted MAC addresses, which can be read and impersonated by a hacker. Use the Push 'N' Connect feature (Wi-Fi Protected Setup). For more information, see "Using Push 'N' Connect (Wi-Fi Protected Setup)" on page 4-7. Wi-Fi Protected Setup provides easy setup by means of a push button. Older wireless adapters and devices might not support this. Check whether devices are WPS enabled. Securing My Wireless 4-3 v1.1, May 2008