Samsung NP-X360 User Manual Vista Ver.1.8 (English) - Page 151
TPM (Trusted Platform Module, Optional), Before Starting TPM
 |
UPC - 036725721203
View all Samsung NP-X360 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 151 highlights
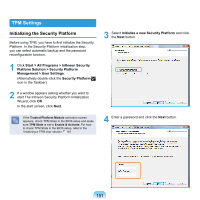
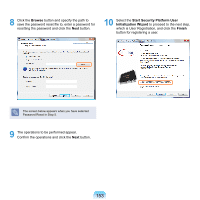
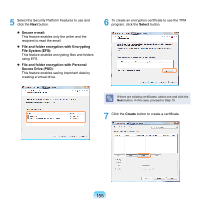
TPM (Trusted Platform Module, Optional) TPM (Trusted Platform Module) is a powerful hardware-based security solution that protects important authentication information such as user passwords from malicious users. If TPM is used with the TPM program, it protects your personal information such as e-mails as well as protecting your system from unauthorized access attempts by malicious users. Before You Start! The program versions described in this manual are subject to change and the screen images and terms in this manual may differ from actual ones. Before Starting TPM You can use the following TPM functions. File Encryption Function: Using this function, you can protect your files and folders by encrypting them. (The EFS function: Encrypt File System). Personal Secure Drive Function: Using this function, you can create a virtual, secure drive so as to safely use important files and folders. (The PSD function: Personal Secure Drive). Initializing and Reconfiguring the TPM Chip: Using this function, you can initialize and reconfigure the authentication information saved on the TPM chip. To use the TPM program, you have to first complete the following steps. 1 Initializing the Security Platform Configure the TPM program password, whether to use automatic backup, and the backup location. 2 Registering a Security Platform User Select the TPM user password and functions to be used and create an encrypted certificate for the TPM user. For more detailed procedures on using the TPM program, refer to program Help. 150