TP-Link 10GE T1700G-28TQUN V1 User Guide - Page 37
SSH Config
 |
View all TP-Link 10GE manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 37 highlights
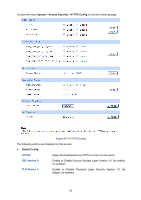
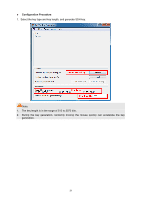
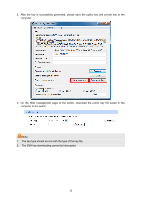
CipherSuite Config RSA_WITH_RC4_128_MD5: RSA_WITH_RC4_128_SHA: RSA_WITH_DES_CBC_SHA: RSA_WITH_3DES_EDE_CBC_SHA: Key exchange with RC4 128-bit encryption and MD5 for message digest. By default, it's enabled. Key exchange with RC4 128-bit encryption and SHA for message digest. By default, it's enabled. Key exchange with DES-CBC for message encryption and SHA for message digest. By default, it's enabled. Key exchange with 3DES and DES-EDE3-CBC for message encryption and SHA for message digest. By default, it's enabled. Session Config Session Timeout: If you do nothing with the Web management page within the timeout time, the system will log out automatically. If you want to reconfigure, please login again. Access User Number Number Control: Admin Number: Guest Number: Select Enable/Disable the Number Control function. Enter the maximum number of the users logging on to the Web management page as Admin. Enter the maximum number of the users logging on to the Web management page as Guest. Certificate Download Certificate File: Select the desired certificate to download to the switch. The certificate must be BASE64 encoded. Key Download Key File: Select the desired key to download to the switch. The key must be BASE64 encoded. Note: 1. The SSL certificate and key downloaded must match each other; otherwise the HTTPS connection will not work. 2. To establish a secured connection using https, please enter https:// into the URL field of the browser. 3. It may take more time for https connection than that for http connection, because https connection involves authentication, encryption and decryption etc. 4.4.4 SSH Config As stipulated by IETF (Internet Engineering Task Force), SSH (Secure Shell) is a security protocol established on application and transport layers. SSH-encrypted-connection is similar to a telnet connection, but essentially the old telnet remote management method is not safe, because the password and data transmitted with plain-text can be easily intercepted. SSH can provide 27