ZyXEL GS1510-24 User Guide - Page 123
Web Authentication
 |
View all ZyXEL GS1510-24 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 123 highlights
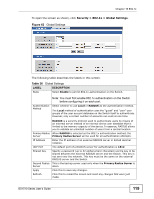
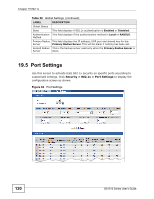
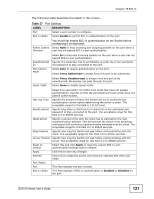
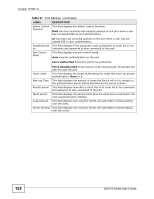
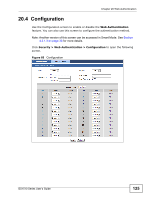
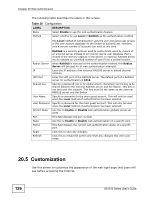
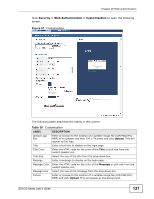
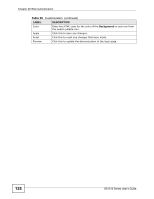
CHAPTER 20 Web Authentication 20.1 Overview This feature is used to authenticate users before they can access a website on the Internet. The Switch can authenticate users who try to log in based on user accounts configured on the Switch itself (see Section 23.2 on page 143). The Switch can also use an external authentication server to authenticate a larger number of users. This external method of authentication uses the RADIUS (Remote Authentication Dial In User Service, RFC 2138, 2139) protocol to validate users. When a user on an enabled port accesses the Internet, a customized web login page will display. User accounts with "User" or "Guest" privileges can login past this screen and access the Internet. 20.2 What You Can Do • Use the Configuration screen (Section 20.4 on page 125) to configure the authentication method and port settings. • Use the Customization screen (Section 20.5 on page 126) to configure the appearance of the web login screen that users will see. 20.3 What You Need to Know Web authentication allows the network administrator to set a username and password for Internet access on a particular port. This feature could be used on a guest terminal, for example in a company meeting room, where guests are allowed to connect to the Internet but not the local network (which is thereby kept secure). GS1510 Series User's Guide 123