Cisco NM-8B-U User Guide - Page 117
Verifying Dynamic Addresses, show mac, address, table dynamic, clear mac-address-table secure
 |
UPC - 074632001001
View all Cisco NM-8B-U manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 117 highlights
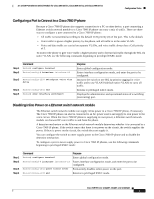
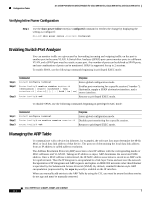
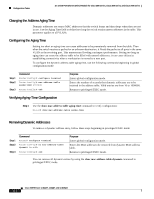
16- and 36-Port Ethernet Switch Module for Cisco 2600 Series, Cisco 3600 Series, and Cisco 3700 Series Configuration Tasks Verifying Dynamic Addresses Step 1 Use the show mac-address-table dynamic command to verify configuration: Router# show mac-address-table dynamic Adding Secure Addresses The secure address table contains secure MAC addresses and their associated ports and VLANs. A secure address is a manually entered unicast address that is forwarded to only one port per VLAN. If you enter an address that is already assigned to another port, the switch reassigns the secure address to the new port. You can enter a secure port address even when the port does not yet belong to a VLAN. When the port is later assigned to a VLAN, packets destined for that address are forwarded to the port. To add a secure address, use the following commands beginning in privileged EXEC mode: Step 1 Step 2 Step 3 Command Router# configure terminal Router(config)# mac-address-table secure address hw-addr interface interface-id vlan vlan-id Router(config)# end Purpose Enters global configuration mode. Enters the MAC address, its associated port, and the VLAN ID. Returns to privileged EXEC mode. To remove a secure address, use the following commands beginning in privileged EXEC mode: Step 1 Step 2 Step 3 Command Router# configure terminal Router(config)# no mac-address-table secure hw-addr vlan vlan-id Router(config)# end Purpose Enters global configuration mode. Enters the secure MAC address, its associated port, and the VLAN ID to be removed. Returns to privileged EXEC mode. You can remove all secure addresses by using the clear mac-address-table secure command in privileged EXEC mode. Verifying Secure Addresses Step 1 Use the show mac-address-table secure command to verify configuration: Router# show mac-address-table secure Cisco IOS Release 12.2(2)XT, 12.2(8)T, and 12.2(15)ZJ 117