HP GbE2c HP GbE2c Ethernet Blade Switch for c-Class BladeSystem ISCLI Referenc - Page 85
TACACS+ server configuration, show radius-server
 |
UPC - 808736802215
View all HP GbE2c manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 85 highlights
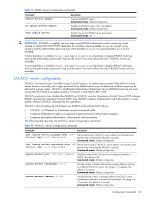
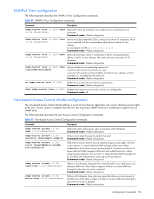
Table 78 RADIUS Server Configuration commands Command radius-server enable no radius-server enable show radius-server Description Enables the RADIUS server. Command mode: Global configuration Disables the RADIUS server. This is the default. Command mode: Global configuration Displays the current RADIUS server parameters. Command mode: All IMPORTANT: If RADIUS is enabled, you must login using RADIUS authentication when connecting via the console or Telnet/SSH/HTTP/HTTPS. Backdoor for console is always enabled, so you can connect using noradius and the administrator password even if the backdoor (telnet) or secure backdoor (secbd) are disabled. If Telnet backdoor is enabled (telnet ena), type in noradius as a backdoor to bypass RADIUS checking, and use the administrator password to log into the switch. The switch allows this even if RADIUS servers are available. If secure backdoor is enabled (secbd ena), type in noradius as a backdoor to bypass RADIUS checking, and use the administrator password to log into the switch. The switch allows this only if RADIUS servers are not available. TACACS+ server configuration TACACS+ (Terminal Access Controller Access Control System) is an authentication protocol that allows a remote access server to forward a user's logon password to an authentication server to determine whether access can be allowed to a given system. TACACS+ and Remote Authentication Dial-In User Service (RADIUS) protocols are more secure than the TACACS encryption protocol. TACACS+ is described in RFC 1492. TACACS+ protocol is more reliable than RADIUS, as TACACS+ uses the Transmission Control Protocol (TCP) whereas RADIUS uses the User Datagram Protocol (UDP). Also, RADIUS combines authentication and authorization in a user profile, whereas TACACS+ separates the two operations. TACACS+ offers the following advantages over RADIUS as the authentication device: • TACACS+ is TCP-based, so it facilitates connection-oriented traffic. • It supports full-packet encryption, as opposed to password-only in authentication requests. • It supports decoupled authentication, authorization, and accounting. The following table describes the TACACS+ Server Configuration commands. Table 79 TACACS+ Server Configuration commands Command Description [no] tacacs-server primary-host key Defines the primary TACACS+ server address and shared secret between the switch and the TACACS+ server(s). Command mode: Global configuration [no] tacacs-server secondary-host key between the switch and the TACACS+ server(s). Command mode: Global configuration tacacs-server port Enter the number of the TCP port to be configured, between 1 65000. The default is 49. Command mode: Global configuration tacacs-server retransmit Sets the number of failed authentication requests before switching to a different TACACS+ server. The range is 1-3 requests. The default is 3 requests. Command mode: Global configuration tacacs-server timeout Sets the amount of time, in seconds, before a TACACS+ server authentication attempt is considered to have failed. The range is 415 seconds. The default is 5 seconds. Command mode: Global configuration Configuration Commands 85