ZyXEL ZyWALL 5 User Guide - Page 370
IPSec VPN, ZyWALL 5/35/70 Series User's Guide, SECURITY > VPN > VPN Rules IKE >
 |
View all ZyXEL ZyWALL 5 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 370 highlights
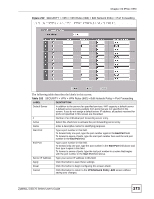
Chapter 19 IPSec VPN Table 102 SECURITY > VPN > VPN Rules (IKE) > Edit Network Policy (continued) LABEL DESCRIPTION Port Forwarding Rules If you are configuring a Many-to-One rule, click this button to go to a screen where you can configure port forwarding for your VPN tunnels. The VPN network policy port forwarding rules let the ZyWALL forward traffic coming in through the VPN tunnel to the appropriate IP address. Type Select One-to-One to translate a single (static) IP address on your LAN to a single virtual IP address. Select Many-to-One to translate a range of (static) IP addresses on your LAN to a single virtual IP address. Many-to-one rules are for traffic going out from your LAN, through the VPN tunnel, to the remote network. Use port forwarding rules to allow incoming traffic from the remote network. Select Many One-to-One to translate a range of (static) IP addresses on your LAN to a range of virtual IP addresses. Private Starting IP Address Specify the IP addresses of the devices behind the ZyWALL that can use the VPN tunnel. When you select One-to-One in the Type field, enter the (static) IP address of a computer on the LAN behind your ZyWALL. When you select Many-to-One or Many One-to-One in the Type field, enter the beginning (static) IP address in a range of computers on the LAN behind your ZyWALL. Private Ending IP Address When you select Many-to-One or Many One-to-One in the Type field, enter the ending (static) IP address in a range of computers on the LAN behind your ZyWALL. Virtual Starting IP Address Enter the (static) IP addresses that represent the translated private IP addresses. These must correspond to the remote IPSec router's configured remote IP addresses. When you select One-to-One or Many-to-One in the Type field, enter an IP address as the translated IP address. Many-to-one rules are only for traffic going to the remote network. Use port forwarding rules to allow incoming traffic from the remote network. When you select Many One-to-One in the Type field, enter the beginning IP address of a range of translated IP addresses. Virtual Ending IP Address When you select Many One-to-One in the Type field, enter the ending (static) IP address of a range of translated IP addresses. The size of the private address range must be equal to the size of the translated virtual address range. Local Network Specify the IP addresses of the devices behind the ZyWALL that can use the VPN tunnel. The local IP addresses must correspond to the remote IPSec router's configured remote IP addresses. Two active SAs cannot have the local and remote IP address(es) both the same. Two active SAs can have the same local or remote IP address, but not both. You can configure multiple SAs between the same local and remote IP addresses, as long as only one is active at any time. Address Type Use the drop-down list box to choose Single Address, Range Address, or Subnet Address. Select Single Address for a single IP address. Select Range Address for a specific range of IP addresses. Select Subnet Address to specify IP addresses on a network by their subnet mask. Starting IP Address When the Address Type field is configured to Single Address, enter a (static) IP address on the LAN behind your ZyWALL. When the Address Type field is configured to Range Address, enter the beginning (static) IP address, in a range of computers on the LAN behind your ZyWALL. When the Address Type field is configured to Subnet Address, this is a (static) IP address on the LAN behind your ZyWALL. 370 ZyWALL 5/35/70 Series User's Guide