HP 6125G HP 6125G & 6125G/XG Blade Switches Security Command Reference - Page 104
Challenge Handshake Authentication Protocol CHAP to communicate with the RADIUS server.
 |
View all HP 6125G manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 104 highlights
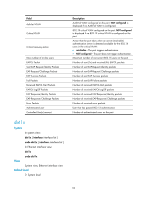
View undo dot1x authentication-method System view Default level 2: System level Parameters chap: Sets the access device to perform Extensible Authentication Protocol (EAP) termination and use the Challenge Handshake Authentication Protocol (CHAP) to communicate with the RADIUS server. eap: Sets the access device to relay EAP packets, and supports any of the EAP authentication methods to communicate with the RADIUS server. pap: Sets the access device to perform EAP termination and use the Password Authentication Protocol (PAP) to communicate with the RADIUS server. Description Use dot1x authentication-method to specify an EAP message handling method. Use undo dot1x authentication-method to restore the default. By default, the network access device performs EAP termination and uses CHAP to communicate with the RADIUS server. The network access device terminates or relays EAP packets: 1. In EAP termination mode, the access device re-encapsulates and sends the authentication data from the client in standard RADIUS packets to the RADIUS server, and performs either CHAP or PAP authentication with the RADIUS server. In this mode the RADIUS server supports only MD5-Challenge EAP authentication, and "username+password" EAP authentication initiated by an iNode client. • PAP transports usernames and passwords in clear text. The authentication method applies to scenarios that do not require high security. To use PAP, the client must be an HP iNode 802.1X client. • CHAP transports username in plaintext and encrypted password over the network. It is more secure than PAP. 2. In EAP relay mode, the access device relays EAP messages between the client and the RADIUS server. The EAP relay mode supports multiple EAP authentication methods, such as MD5-Challenge, EAP-TL, and PEAP. To use this mode, you must make sure that the RADIUS server supports the EAP-Message and Message-Authenticator attributes, and uses the same EAP authentication method as the client. If this mode is used, the user-name-format command configured in RADIUS scheme view does not take effect. For more information about the user-name-format command, see "RADIUS configuration commands." Local authentication supports PAP and CHAP. If RADIUS authentication is used, you must configure the network access device to use the same authentication method (PAP, CHAP, or EAP) as the RADIUS server. Related commands: display dot1x. Examples # Enable the access device to terminate EAP packets and perform PAP authentication with the RADIUS server. system-view 95