Cisco NME-16ES-1G User Guide - Page 61
Enabling 802.1x Authentication
 |
UPC - 882658036101
View all Cisco NME-16ES-1G manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 61 highlights
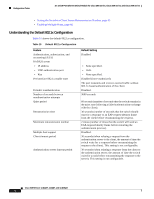
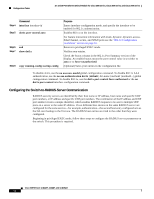
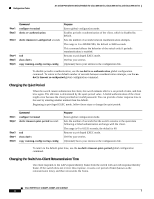
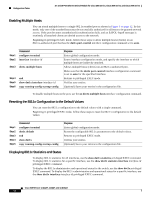
16- and 36-Port Ethernet Switch Module for Cisco 2600 Series, Cisco 3600 Series, and Cisco 3700 Series Configuration Tasks 802.1x Configuration Guidelines These are the 802.1x authentication configuration guidelines: • When the 802.1x protocol is enabled, ports are authenticated before any other Layer 2 feature is enabled. • The 802.1x protocol is supported on Layer 2 static-access ports, but it is not supported on these port types: - Trunk port-If you try to enable 802.1x on a trunk port, an error message appears, and 802.1x is not enabled. If you try to change the mode of an 802.1x-enabled port to trunk, the port mode is not changed. - EtherChannel port-Before enabling 802.1x on the port, you must first remove the port from the EtherChannel before enabling 802.1x on it. If you try to enable 802.1x on an EtherChannel or on an active port in an EtherChannel, an error message appears, and 802.1x is not enabled. If you enable 802.1x on a not-yet active port of an EtherChannel, the port does not join the EtherChannel. - Switch Port Analyzer (SPAN) destination port-You can enable 802.1x on a port that is a SPAN destination port; however, 802.1x is disabled until the port is removed as a SPAN destination. You can enable 802.1x on a SPAN source port. Enabling 802.1x Authentication To enable 802.1x port-based authentication, you must enable AAA and specify the authentication method list. A method list describes the sequence and authentication methods to be queried to authenticate a user. The software uses the first method listed to authenticate users; if that method fails to respond, the software selects the next authentication method in the method list. This process continues until there is successful communication with a listed authentication method or until all defined methods are exhausted. If authentication fails at any point in this cycle, the authentication process stops, and no other authentication methods are attempted. Beginning in privileged EXEC mode, follow these steps to configure 802.1x port-based authentication. This procedure is required. Step 1 Step 2 Step 3 Command configure terminal aaa new-model aaa authentication dot1x {default | listname} method1 [method2...] Purpose Enters global configuration mode. Enables AAA. Creates an 802.1x authentication method list. To create a default list that is used when a named list is not specified in the authentication command, use the default keyword followed by the methods that are to be used in default situations. The default method list is automatically applied to all interfaces. Enter at least one of these keywords: • group radius-Use the list of all RADIUS servers for authentication. • none-Use no authentication. The client is automatically authenticated without the switch using the information supplied by the client. Cisco IOS Release 12.2(2)XT, 12.2(8)T, and 12.2(15)ZJ 61