Cisco NME-16ES-1G User Guide - Page 82
Command, Purpose, con terminal, access-list, permit, remark, show access-lists
 |
UPC - 882658036101
View all Cisco NME-16ES-1G manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 82 highlights
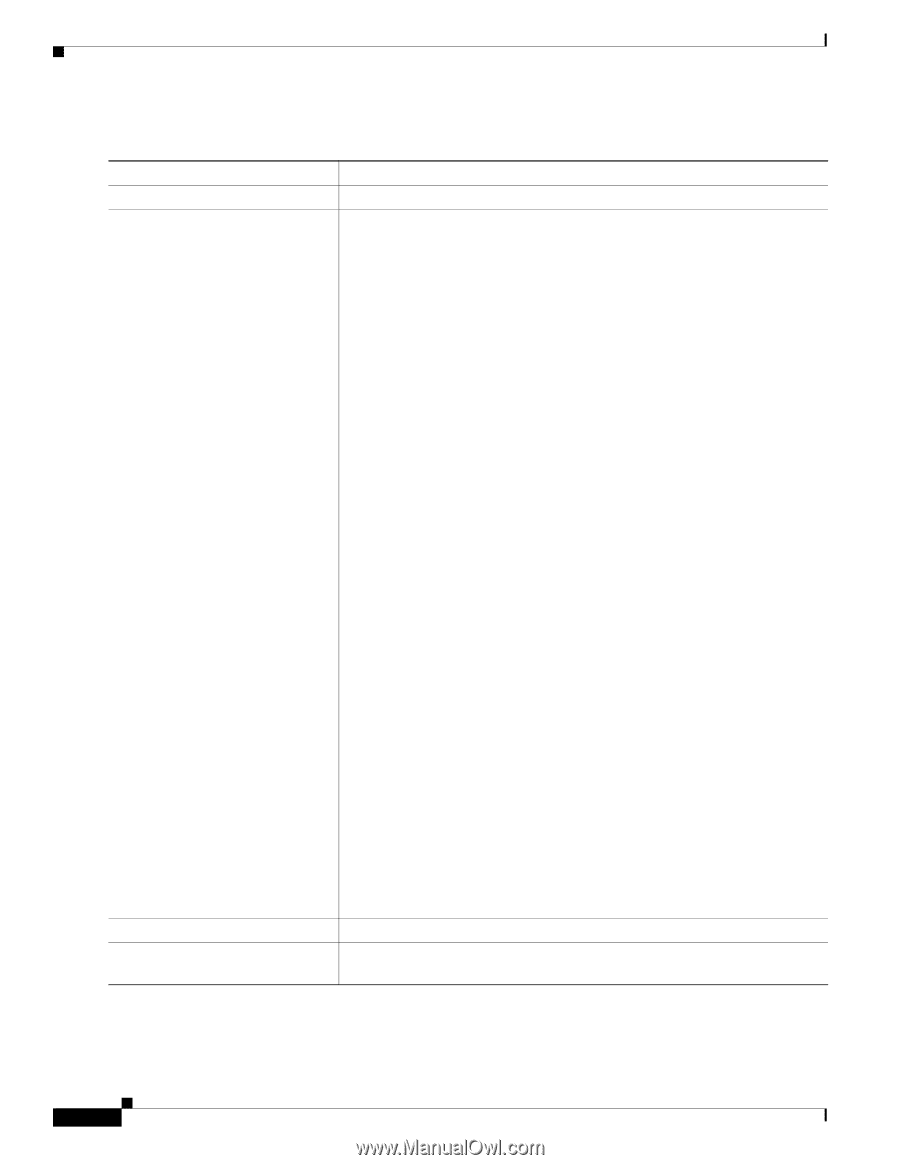
Configuration Tasks 16- and 36-Port Ethernet Switch Module for Cisco 2600 Series, Cisco 3600 Series, and Cisco 3700 Series Beginning in privileged EXEC mode, follow these steps to create an extended ACL: Step 1 Step 2 Command Purpose configure terminal Enters global configuration mode. access-list access-list-number {deny | permit | remark} protocol {source source-wildcard | host source | any} [operator port] {destination destination-wildcard | host destination | any} [operator port] Defines an extended IP access list and the access conditions. The access-list-number is a decimal number from 100 to 199 or 2000 to 2699. Enter deny or permit to specify whether to deny or permit the packet if conditions are matched. For protocol, enter the name or number of an IP protocol: ip, tcp, or udp. To match any Internet protocol (including TCP and UDP), use the keyword ip. Note This step includes options for most IP protocols. Step 3 Step 4 show access-lists [number | name] copy running-config startup-config The source is the number of the network or host from which the packet is sent. The source-wildcard applies wildcard bits to the source. The destination is the network or host number to which the packet is sent. Defines a destination or source port. • The operator can be only eq (equal). • If operator is after source source-wildcard, conditions match when the source port matches the defined port. • If operator is after destination destination-wildcard, conditions match when the destination port matches the defined port. • The port is a decimal number or name of a TCP or UDP port. The number can be from 0 to 65535. • Use TCP port names only for TCP traffic. • Use UDP port names only for UDP traffic. The destination-wildcard applies wildcard bits to the destination. Source, source-wildcard, destination, and destination-wildcard can be specified in three ways: • The 32-bit quantity in dotted-decimal format. • The keyword any as an abbreviation for source and source-wildcard of 0.0.0.0 255.255.255.255 or any source host. • The keyword host, followed by the 32-bit quantity in dotted-decimal format, as an abbreviation for a single host with source and source-wildcard of source 0.0.0.0. Note Only the ip, tcp, and udp protocols are supported on Ethernet switch interfaces. Verifies the access list configuration. (Optional) Saves your entries in the configuration file. Cisco IOS Release 12.2(2)XT, 12.2(8)T, and 12.2(15)ZJ 82