Cisco NME-16ES-1G User Guide - Page 94
Classifying, Policing, and Marking Traffic by Using Policy Maps, class, access-group
 |
UPC - 882658036101
View all Cisco NME-16ES-1G manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 94 highlights
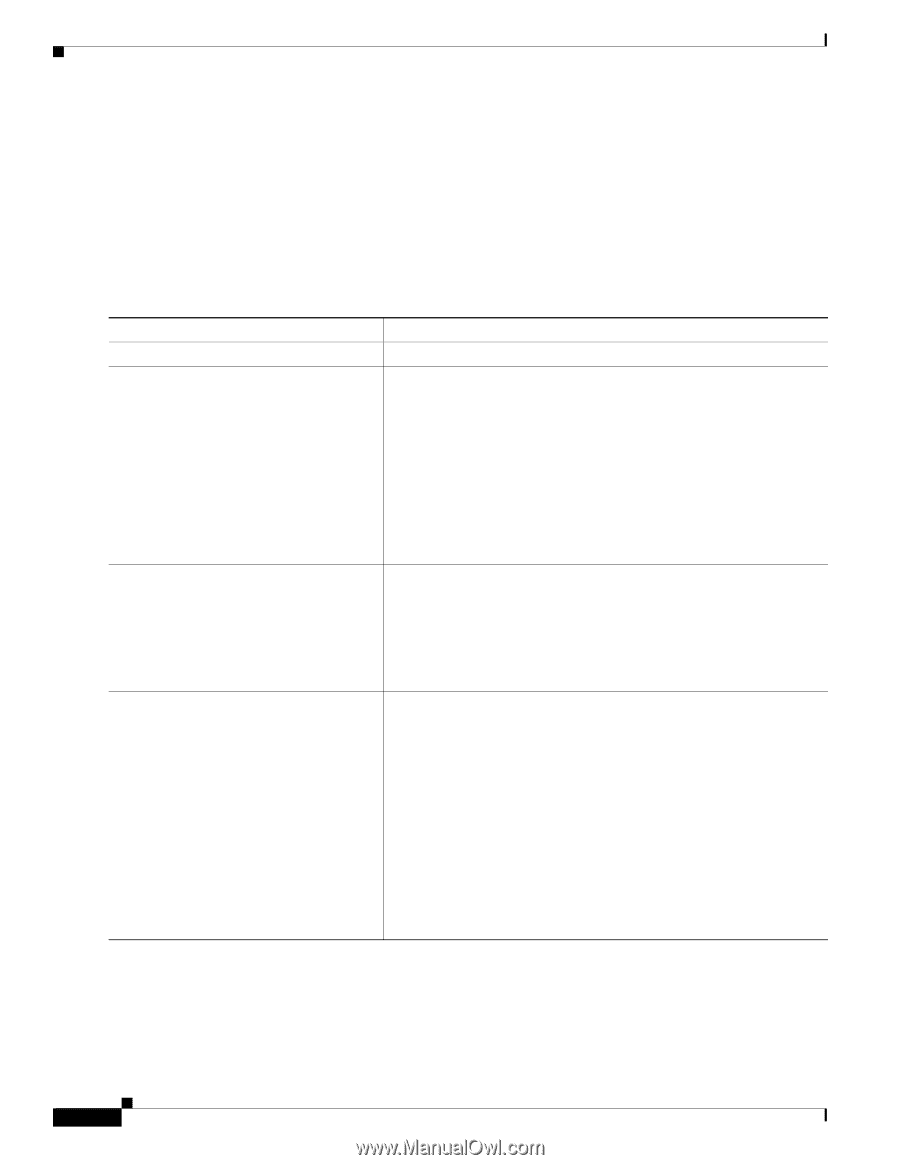
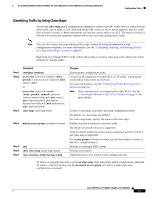
Configuration Tasks 16- and 36-Port Ethernet Switch Module for Cisco 2600 Series, Cisco 3600 Series, and Cisco 3700 Series Classifying, Policing, and Marking Traffic by Using Policy Maps A policy map specifies which traffic class to act on. Actions can include trusting the CoS or DSCP values in the traffic class; setting a specific DSCP value in the traffic class; and specifying the traffic bandwidth limitations for each matched traffic class (policer) and the action to take when the traffic is out of profile (marking). A separate policy-map class can exist for each type of traffic received through an interface. You can attach only one policy map per interface in the input direction. Beginning in privileged EXEC mode, follow these steps to create a policy map: Step 1 Step 2 Step 3 Command configure terminal access-list access-list-number {deny | permit} {source source-wildcard | host source | any} or access-list access-list-number {deny | permit | remark} protocol {source source-wildcard | host source | any}[operator port] {destination destination-wildcard | host destination | any} [operator port] policy-map policy-map-name Step 4 class class-map-name [access-group acl-index-or-name] Purpose Enters global configuration mode. Creates an IP standard or extended ACL for IP traffic, repeating the command as many times as necessary. For more information, see the "Classifying Traffic by Using ACLs" section on page 91. Note Deny statements are not supported for QoS ACLS. See the "Classification Based on QoS ACLs" section on page 32 for more details. Creates a policy map by entering the policy map name, and enter policy-map configuration mode. By default, no policy maps are defined. The default behavior of a policy map is to set the DSCP to 0 if the packet is an IP packet and to set the CoS to 0 if the packet is tagged. No policing is performed. Defines a traffic classification, and enter policy-map class configuration mode. By default, no policy map class maps are defined. If a traffic class has already been defined by using the class-map global configuration command, specify its name for class-map-name in this command. For access-group acl-index-or-name, specify the number or name of the ACL created in Step 2. Note In a policy map, the class named class-default is not supported. The switch does not filter traffic based on the policy map defined by the class class-default policy-map configuration command. Cisco IOS Release 12.2(2)XT, 12.2(8)T, and 12.2(15)ZJ 94