Cisco NME-16ES-1G User Guide - Page 93
Classifying Traffic by Using Class Maps, show class-map
 |
UPC - 882658036101
View all Cisco NME-16ES-1G manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 93 highlights
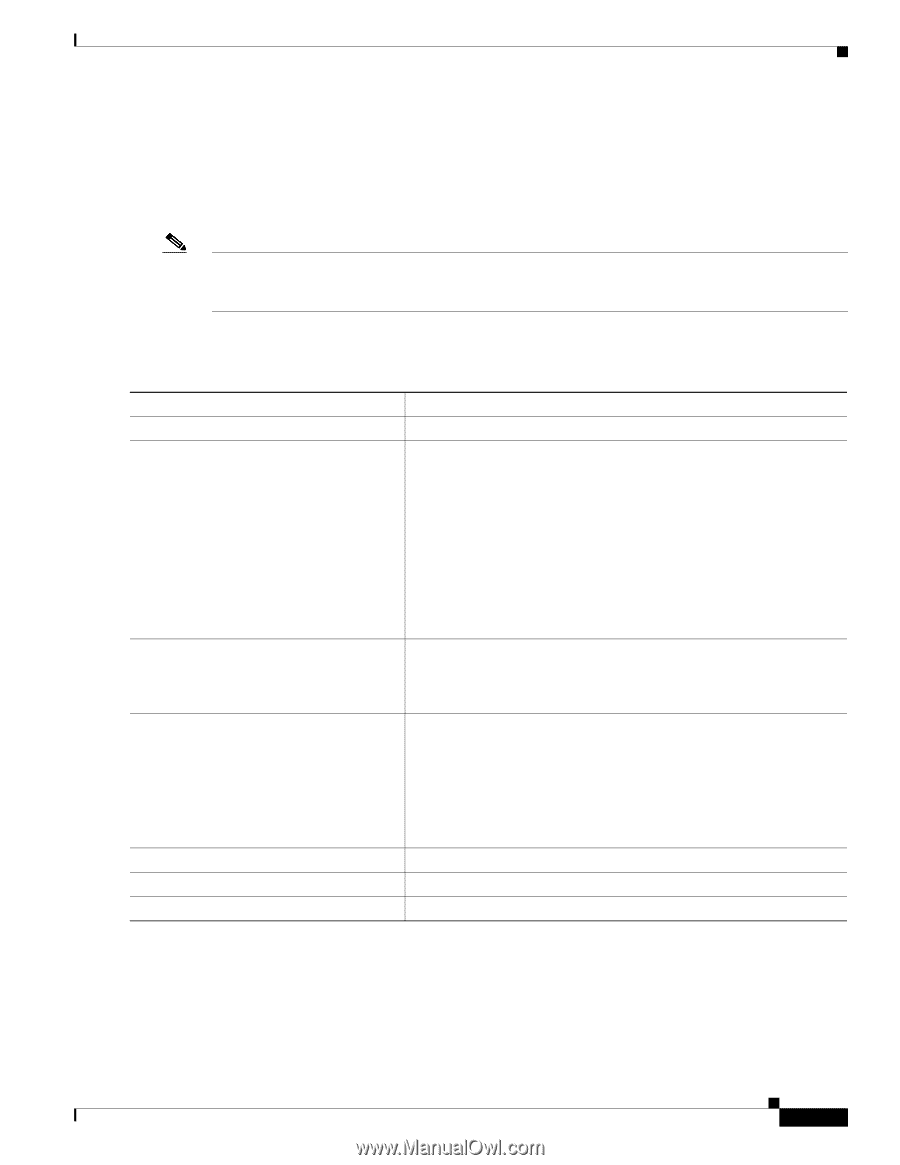
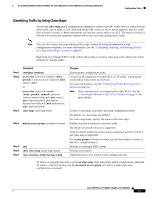
16- and 36-Port Ethernet Switch Module for Cisco 2600 Series, Cisco 3600 Series, and Cisco 3700 Series Configuration Tasks Classifying Traffic by Using Class Maps You use the class-map global configuration command to isolate a specific traffic flow (or class) from all other traffic and to name it. The class map defines the criteria to use to match against a specific traffic flow to further classify it. Match statements can include criteria such as an ACL. The match criterion is defined with one match statement entered within the class-map configuration mode. Note You can also create class maps during policy map creation by using the class policy-map configuration command. For more information, see the "Classifying, Policing, and Marking Traffic by Using Policy Maps" section on page 94. Beginning in privileged EXEC mode, follow these steps to create a class map and to define the match criterion to classify traffic: Step 1 Step 2 Step 3 Command configure terminal access-list access-list-number {deny | permit} {source source-wildcard | host source | any} or access-list access-list-number {deny | permit | remark} protocol {source source-wildcard | host source | any} [operator port] {destination destination-wildcard | host destination | any} [operator port] class-map class-map-name Step 4 match access-group acl-index-or-name Step 5 Step 6 Step 7 end show class-map [class-map-name] copy running-config startup-config Purpose Enters global configuration mode. Creates an IP standard or extended ACL for IP traffic, repeating the command as many times as necessary. For more information, see the "Classifying Traffic by Using ACLs" section on page 91. Note Deny statements are not supported for QoS ACLS. See the "Classification Based on QoS ACLs" section on page 32 for more details. Creates a class map, and enter class-map configuration mode. By default, no class maps are defined. For class-map-name, specify the name of the class map. Defines the match criterion to classify traffic. By default, no match criterion is supported. Only one match criterion per class map is supported, and only one ACL per class map is supported. For access-group acl-index-or-name, specify the number or name of the ACL created in Step 3. Returns to privileged EXEC mode. Verifies your entries. (Optional) Saves your entries in the configuration file. To delete an existing class map, use the no class-map class-map-name global configuration command. To remove a match criterion, use the no match access-group acl-index-or-name class-map configuration command. Cisco IOS Release 12.2(2)XT, 12.2(8)T, and 12.2(15)ZJ 93