D-Link DWC-2000-AP32-LIC User Manual - Page 67
Configure AP WIDS Settings
 |
View all D-Link DWC-2000-AP32-LIC manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 67 highlights
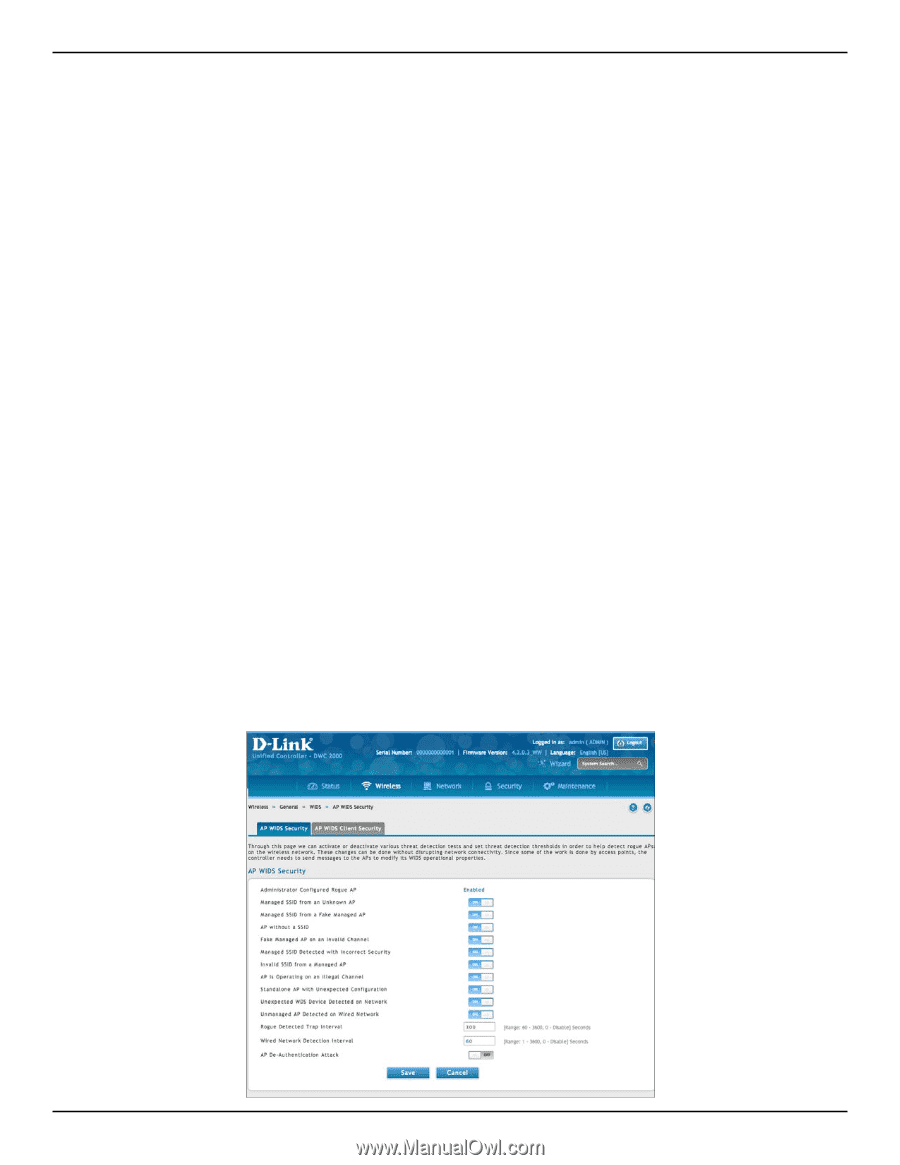
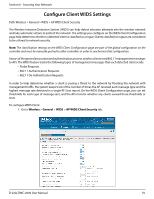
Section 6 - Securing Your Network WIDS The Wireless Intrusion Detection System (WIDS) can help detect intrusion attempts into the wireless network and take automatic actions to protect the network. Configure AP WIDS Settings Path: Wireless > General > WIDS > AP WIDS Security The WIDS AP Configuration page allows you to activate or deactivate various threat detection tests and set threat detection thresholds in order to help detect rogue APs on the wireless network. These changes can be done without disrupting network connectivity. Since some of the work is done by access points, the controller needs to send messages to the APs to modify its WIDS operational properties. Note: The classification settings on the WIDS AP Configuration page are part of the global configuration on the controller and must be manually pushed to other controllers in order to synchronize that configuration. Many of the tests are focused on identifying APs that are advertising managed SSIDs, but are not in fact managed APs. Detecting such an AP means that a network is either miss‐configured or that a hacker set up a honeypot AP in the attempt to collect passwords or other secure information. Although operational mode radios can detect most threats, the sentry radios detect the threats faster, especially when a potential rogue is operating on a different channel from any of the managed AP radios. The number of deployed sentry radios should be sufficient to provide coverage by one sentry radio in every geographical location within the network. A denser sentry deployment may be desirable in order to improve rogue or interferer signal triangulation. To configure WIDS AP: 1. Go to Wireless > General > WIDS > AP WIDS Security tab. D-Link DWC-2000 User Manual 67