D-Link DWC-2000-AP32-LIC User Manual - Page 69
Securing Your Network
 |
View all D-Link DWC-2000-AP32-LIC manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 69 highlights
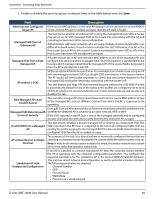
Section 6 - Securing Your Network Field Unexpected WDS Device Detection on Network Unmanaged AP Detection on Wired Network Rogue Detected Trap Interval Wired Network Detection Interval AP De-Authentication Attack Description If the AP is classified as a Managed or Unknown AP and wireless distribution system (WDS) traffic is detected on the AP, then the AP is considered to be Rogue. Only stand‐ alone APs that are explicitly allowed to operate in WDS mode are not reported as rogues by this test. This test checks whether the AP is detected on the wired network. If the AP state is Unknown, then the test changes the AP state to Rogue. The flag indicating whether AP is detected on the wired network is reported as part of the RF Scan report. If AP is managed and is detected on the network then the controller simply reports this fact and doesn't change the AP state to Rogue. In order for the wireless system to detect this threat, the wireless network must contain one or more radios that operate in sentry mode. Specify the interval, in seconds, between transmissions of the SNMP trap telling the administrator that rogue APs are present in the RF Scan database. If you set the value to 0, the trap is never sent. Specify the number of seconds that the AP waits before starting a new wired network detection cycle. If you set the value to 0, wired network detection is disabled. Enable or disable the AP de‐authentication attack. The wireless controller can protect against rogue APs by sending de‐authentication messages to the rogue AP. The de‐ authentication attack feature must be globally enabled in order for the wireless system to do this function. Make sure that no legitimate APs are classified as rogues before enabling the attack feature. This feature is disabled by default. D-Link DWC-2000 User Manual 69