D-Link DWC-2000-AP32-LIC User Manual - Page 71
Not Present in OUI Database
 |
View all D-Link DWC-2000-AP32-LIC manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 71 highlights
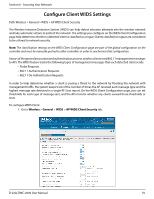
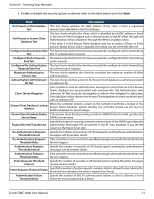
Section 6 - Securing Your Network 2. Enable or disable the security options as desired (refer to the table below) and click Save. Field Description Not Present in OUI Database This test checks whether the MAC address of the client is from a registered Test manufacturer identified in the OUI database. Not Present in Known Client Database Test This test checks whether the client, which is identified by its MAC address, is listed in the Known Client Database and is allowed access to the AP either through the Authentication Action of Grant or through the White List global action. If the client is in the Known Client Database and has an action of Deny, or if the action is Global Action and it is globally set to Black List, the client fails this test. Configured Authentication Rate This test checks whether the client has exceeded the configured rate for transmitting Test 802.11 authentication requests. Configured Probe Requests This test checks whether the client has exceeded the configured rate for transmitting Rate Test probe requests. Configured De-Authentication This test checks whether the client has exceeded the configured rate for transmitting Requests Rate Test de‐authentication requests. Maximum Authentication Failures Test This test checks whether the client has exceeded the maximum number of failed authentications. Authentication with Unknown This test checks whether a client in the Known Client database is authenticated with AP Test an unknown AP. Client Threat Mitigation Select enable to send de‐authentication messages to clients that are in the Known Clients database but are associated with unknown APs. The Authentication with Unknown AP Test must also be enabled in order for the mitigation to take place. Select disable to allow clients in the Known Clients database to remain authenticated with an unknown AP. Known Client Database Lookup Method When the controller detects a client on the network it performs a lookup in the Known Client database. Specify whether the controller should use the local or RADIUS database for these lookups. Known Client Database Radius If the known client database lookup method is RADIUS then this field specifies the Server Name RADIUS server name. Specify the interval, in seconds, between transmissions of the SNMP trap telling the Rogue Detected Trap Interval administrator that rogue APs are present in the RF Scan database. If you set the value to 0, the trap is never sent. De-Authentication Requests Specify the number of seconds an AP should spend counting the de‐authentication Threshold Interval messages sent by wireless clients. De-Authentication Requests If the controller receives more than specified messages during the threshold interval Threshold Value the test triggers. Authentication Requests Threshold Interval Specify the number of seconds an AP should spend counting the authentication messages sent by wireless clients. Authentication Requests Threshold Value If the controller receives more than specified messages during the threshold interval the test triggers. Probe Requests Threshold Specify the number of seconds an AP should spend counting the probe messages Interval sent by wireless clients. Probe Requests Threshold Value Specify the number of probe requests a wireless client is allowed to send during the threshold interval before the event is reported as a threat. Authentication Failure Threshold Value Specify the number of 802.1X authentication failures a client is allowed to have before the event is reported as a threat. D-Link DWC-2000 User Manual 71