Netgear DG834Gv3 DG834Gv3 Reference Manual - Page 36
Choosing WEP Authentication and Security Encryption Methods, Apply, Trusted Wireless Stations
 |
View all Netgear DG834Gv3 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 36 highlights
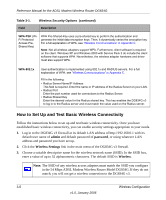
Reference Manual for the ADSL Modem Wireless Router DG834G You can copy and paste the MAC addresses from the modem router's Attached Devices menu into the MAC Address box of this menu. To do this, configure each wireless computer to obtain a wireless link to the modem router. The computer should then appear in the Attached Devices menu. Note: If you are configuring the modem router from a wireless computer whose MAC address is not in the Trusted Wireless Stations list, and you select Trusted Wireless Stations only, you will lose your wireless connection when you click Apply. You must then access the modem router from a wired computer to make any further changes. 6. Make sure the Turn Access Control On check box is selected, then click Apply. Now, only devices on this list will be allowed to wirelessly connect to the DG834G v3. This prevents unauthorized access to your network. Choosing WEP Authentication and Security Encryption Methods Figure 3-5 3-10 v1.0, January 2006 Wireless Configuration