Canon PIXMA MP800R Setup Guide - Page 22
Confirming Settings of your Access Point - mac
 |
View all Canon PIXMA MP800R manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 22 highlights
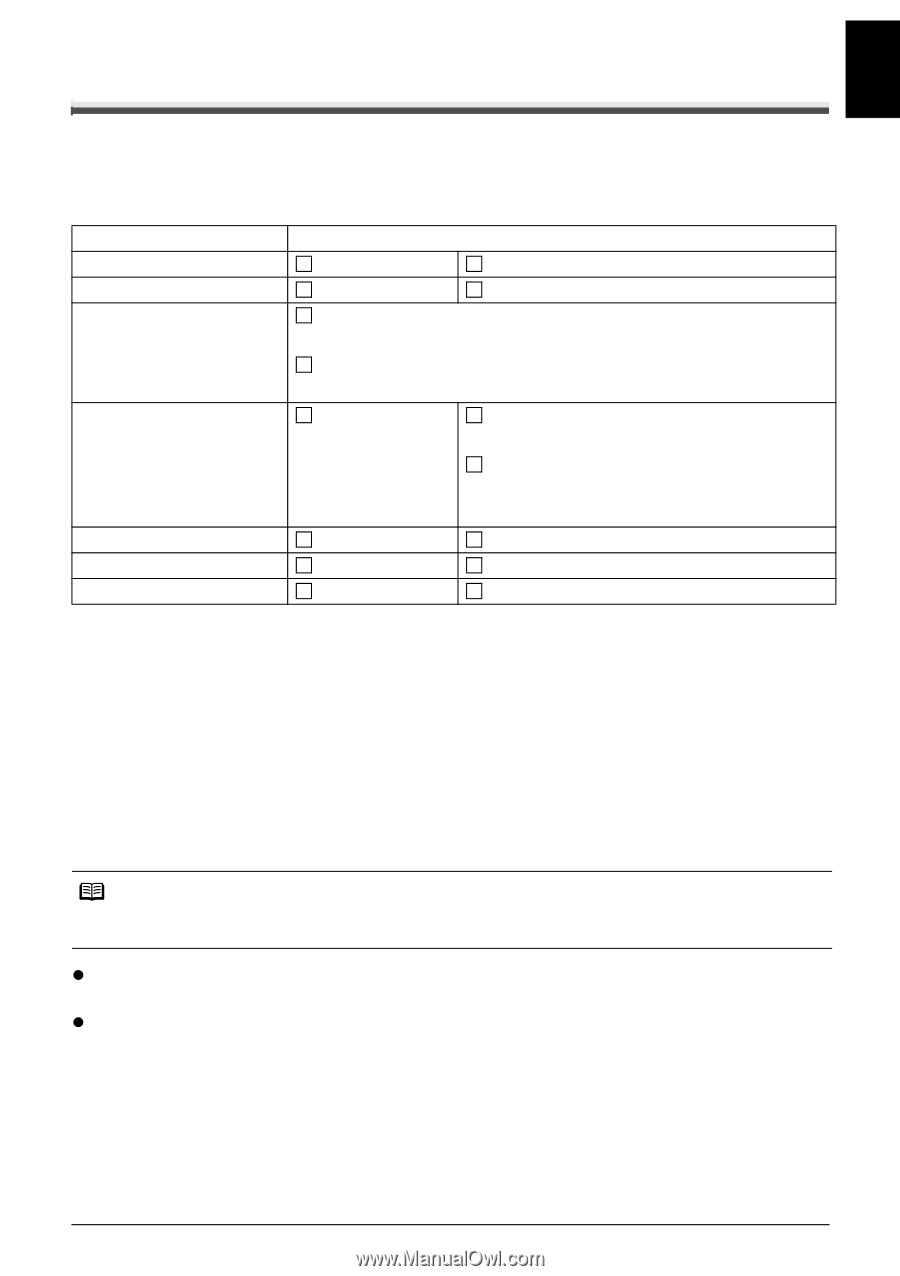
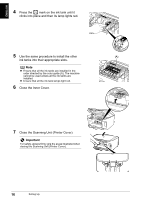
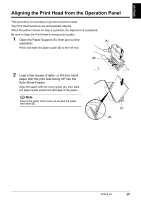
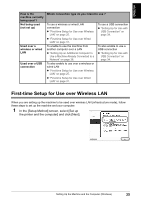
ENGLISH Confirming Settings of your Access Point When setting up the machine to be used over wireless LAN, the machine's network settings are configured to match those of the access point. Therefore, if you are using wireless LAN, we recommend that you confirm the necessary information on the access point before entering the setup process. Check and fill in the table below. SSID/network name Stealth/closed network*1 ANY-Rejection*2 Radio channel Disabled Disabled Automatic Enabled Enabled Channel ( ) : The machine can communicate in channels 1 to 11. Encryption Disabled WEP Enabled key ( ) WPA or WPA2 Enabled*3 key ( ) Encryption (TKIP · AES) MAC address filtering Disabled Enabled IP address filtering Client-to-Client Blocking*4 Disabled Disabled Enabled Enabled *1 In the stealth mode, an access point hides itself by not broadcasting its SSID. The client must specify the SSID set to the access point to detect it. In Macintosh, the stealth mode is called a "closed network". *2 Any rejection is a feature of an access point to hide itself from and/or reject connection with clients whose SSID/network name is set to "ANY". *3 This machine supports the methods below. If you are using another method, change the WPA/ WPA2 settings on the access point and computers to match these. Authentication method: WPA-PSK (WPA Personal) or WPA2-PSK (WPA2 Personal) Encryption method: TKIP or AES *4 If Client-to-Client Blocking is enabled, clients are not allowed to communicate with other clients associated with the same access point. Note For information on how to confirm the settings of the access point, refer to the manual provided with the access point or contact its manufacturer. z If Stealth (closed network) or ANY-Rejection feature is enabled We recommend you to disable it before entering setup. z If MAC address filtering is enabled You must register the machine's MAC address to the access point before entering setup. To confirm the MAC address of the machine, print the machine's network information. See "Printing Out Network Setting Information" on page 72. Confirming the Setup Environment 21