D-Link DGS-3612G Product Manual - Page 406
MAC-based Access Control, MAC-based Access Control Global Settings
 |
UPC - 790069296390
View all D-Link DGS-3612G manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 406 highlights
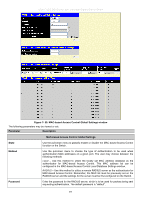
xStack® DGS-3600 Series Layer 3 Managed Gigabit Ethernet Switch MAC-based Access Control The MAC-based Access Control feature will allow users to configure a list of MAC addresses, either locally or on a remote RADIUS server, to be authenticated by the Switch and given access rights based on the configurations set on the Switch of the target VLAN where these authenticated users are placed. For local authentication on the Switch, the user must enter a list of MAC addresses to be accepted through this mechanism using the MAC-based Access Control Global Settings window, as seen below. The user may enter up to 1024 MAC addresses locally on the Switch but only 1024 MAC addresses can be accepted per physical MAC-based Access Control enabled port. Once a MAC addresses has been authenticated by the Switch on the local side, the port where that MAC address resides will be placed in the previously configured target VLAN, where the rights and privileges are set by the switch administrator. If the VLAN Name for the target VLAN is not found by the Switch, the Switch will return the port containing that MAC address to the originating VLAN. If the MAC address is not found and the port is in the Guest VLAN, it will remain in the Guest VLAN, with the associated rights. If the port is not in the guest VLAN, this MAC address will be blocked by the Switch. For remote RADIUS server authentication, the user must first configure the RADIUS server with a list of MAC addresses and relative target VLANs that are to be authenticated on the Switch. Once a MAC address has been discovered by the Switch, the Switch will then query the remote RADIUS server with this potential MAC address, using a RADIUS Access Request packet. If a match is made with this MAC address, the RADIUS server will return a notification stating that the MAC address has been accepted and is to be placed in the target VLAN. If the VID for the target VLAN is not found, the Switch will return the port containing the MAC address to the original VLAN. If the MAC address is not found, and if the port is in the Guest VLAN, it will remain in the Guest VLAN, with the associated rights. If the port is not in the guest VLAN, this MAC address will be blocked by the Switch. Notes about MAC-based Access Control There are certain limitations and regulations regarding the MAC-based Access Control: Once this feature is enabled for a port, the Switch will clear the FDB of that port. MAC-based Access Control is its own entity and is not dependant on other authentication functions on the Switch, such as 802.1X, Web-Based authentication etc. A port accepts a maximum of 1024 authenticated MAC addresses in local mode and 4000 MAC addresses in radius mode per physical port of a VLAN that is not a Guest VLAN. Other MAC addresses attempting authentication on a port with the maximum number of authenticated MAC addresses will be blocked. Ports that have been enabled for Link Aggregation, stacking, 802.1X authentication, 802.1X Guest VLAN, Port Security, GVRP or Web-based authentication cannot be enabled for the MAC-based Authentication. MAC-based Access Control Guest VLAN cannot be a member of a Web-based authentication VLAN. MAC-based Access Control Global Settings The following window is used to set the parameters for the MAC-based Access Control function on the Switch. Here the user can set the running state, method of authentication, RADIUS password and view the Guest VLAN configuration to be associated with the MAC-based Access Control function of the Switch. To enable these Settings, click Security > MAC-based Access Control > MAC-based Access Control Global Settings, as shown below: 390