Motorola WA840GP User Guide - Page 92
Authentication, Encryption, WIRELESS ENCRYPTION METHODS
 |
UPC - 612572118740
View all Motorola WA840GP manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 92 highlights
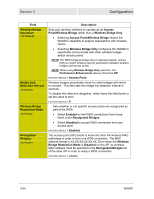
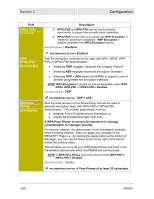
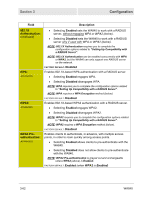
Section 3 Configuration You will find that the wireless security settings on the SECURITY page are essentially broken down into enabling two security components on your network: • Authentication methods - means of establishing identification criteria by which wireless clients are recognized (akin to different types of ID cards). WIRELESS AUTHENTICATION METHODS 1) 802.11 Authentication, which re-uses encryption keys as identification criteria. 2) 802.1X Authentication, which introduces a RADIUS (Remote Authentication Dial-In User Service) authentication server to verify the identity of a client device with a "shared secret" (similar to a password) and dynamically generate an encryption key. 802.1X Authentication can be used with or without 802.11 Authentication. 3) Wi-Fi Protected Access (WPA) authentication, a recent standard issued by the WiFi Alliance, which advocates the use of either 802.1X or a Pre Shared Key (PSK) authentication method, based on enterprise or home wireless use. The PSK method, typically used in home applications, is called WPA-PSK. WPA-PSK uses a pass phrase (similar to a password, but not limited to one word) to automatically generate encryption keys, and does not require a RADIUS server. 4) Wi-Fi Protected Access version 2 (WPA2TM) authentication, an updated standard issued by the Wi-Fi Alliance, but still advocating the use of either 802.1X or a PSK authentication method. The updated PSK method is called WPA2-PSK. WPA2-PSK, like WPA-PSK, uses a pass phrase to automatically generate encryption keys, and does not require a RADIUS server. • Encryption methods - means of encoding data transmitted over the wireless network, so that only devices with a proper decoder can read that data. Encryption methods use "keys" to encode and decode data. WIRELESS ENCRYPTION METHODS 1) Wired Equivalent Privacy (WEP), which requires the manual entry of a 64-bit or 128-bit encryption key. The same key must be used at both ends of the wireless link. WEP uses this key until it is manually changed, making WEP inherently less secure than other encryption methods. WEP is the only encryption method that is compatible with 802.11 or 802.1X authentication. 2) Temporal Key Integrity Protocol (TKIP), a more powerful encryption method which periodically changes the encryption key to increase security. TKIP encryption requires WPA, WPA-PSK, WPA2, or WPA2-PSK authentication. 3) Advanced Encryption Standard (AES), a high-grade encryption method tested to government standards. AES encryption requires WPA, WPA-PSK, WPA2, or WPA2PSK authentication. Remember that securing your wireless network requires that you use the same authentication and encryption methods in the WA840 and in the devices with which it will communicate. If you have a set of wireless devices with varying authentication and/or encryption capabilities, the WA840 can concurrently support multiple methods, accommodating some combinations. 3-58 WA840