McAfee MTP08EMB3RUA Product Guide - Page 90
Connection type and detections of incoming communications, Select, Custom
 |
UPC - 731944568133
View all McAfee MTP08EMB3RUA manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 90 highlights
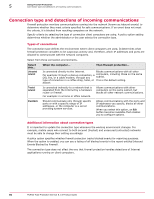
5 Using Firewall Protection Connection type and detections of incoming communications Connection type and detections of incoming communications Firewall protection monitors communications coming into the network (known as inbound events) to determine whether they meet criteria specified for safe communications. If an event does not meet the criteria, it is blocked from reaching computers on the network. Specify criteria by selecting the type of connection client computers are using. A policy option setting determines whether the administrator or the user selects the connection type. Types of connections The connection type defines the environment where client computers are used, It determines what firewall protection considers to be suspicious activity and, therefore, which IP addresses and ports are allowed to communicate with the network computers. Select from three connection environments. Select this... Untrusted network Trusted network When the computer... Then firewall protection... Is connected directly to the Internet. Blocks communications with all other For example: through a dial-up connection, a DSL line, or a cable modem; through any computers, including those on the same subnet. type of connection in a coffee shop, hotel, or This is the default setting. airport. Is connected indirectly to a network that is separated from the Internet by a hardware router or firewall. For example: in a home or office network. Allows communications with other computers on the same subnet, but blocks all other network communications. Custom Should communicate only through specific ports or with a specific range of IP addresses, or the computer is a server providing system services. Allows communications with the ports and IP addresses you specify, blocks all other communications. When you select this option, an Edit button becomes available that enables you to configure options. Additional information about connection types It is important to update the connection type whenever the working environment changes. For example, mobile users who connect to both secured (trusted) and unsecured (untrusted) networks must be able to change their setting accordingly. A policy option specifies whether firewall protection tracks blocked events for reporting purposes. When the option is enabled, you can see a listing of all blocked events in the report entitled Inbound Events Blocked by Firewall. The connection type does not affect the way that firewall protection handles detections of Internet applications running on client computers. 90 McAfee Total Protection Service 5.1.5 Product Guide