ZyXEL NWA-3163 User Guide - Page 236
Certificates > Trusted CAs Details continued
 |
View all ZyXEL NWA-3163 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 236 highlights
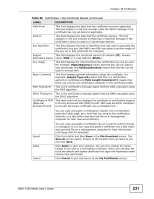
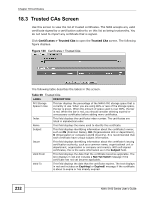
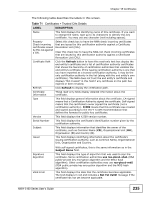
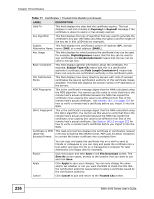
Chapter 18 Certificates Table 71 Certificates > Trusted CAs Details (continued) LABEL DESCRIPTION Valid To This field displays the date that the certificate expires. The text displays in red and includes an Expiring! or Expired! message if the certificate is about to expire or has already expired. Key Algorithm This field displays the type of algorithm that was used to generate the certificate's key pair (the NWA uses RSA encryption) and the length of the key set in bits (1024 bits for example). Subject This field displays the certificate's owner's IP address (IP), domain Alternative Name name (DNS) or e-mail address (EMAIL). Key Usage This field displays for what functions the certificate's key can be used. For example, DigitalSignature means that the key can be used to sign certificates and KeyEncipherment means that the key can be used to encrypt text. Basic Constraint This field displays general information about the certificate. For example, Subject Type=CA means that this is a certification authority's certificate and Path Length Constraint=1 means that there can only be one certification authority in the certificate's path. CRL Distribution Points This field displays how many directory servers with Lists of revoked certificates the issuing certification authority of this certificate makes available. This field also displays the domain names or IP addresses of the servers. MD5 Fingerprint This is the certificate's message digest that the NWA calculated using the MD5 algorithm. You cannot use this value to verify that this is the remote host's actual certificate because the NWA has signed the certificate; thus causing this value to be different from that of the remote host's actual certificate. See Section 18.1.2 on page 222 for how to verify a remote host's certificate before you import it into the NWA. SHA1 Fingerprint This is the certificate's message digest that the NWA calculated using the SHA1 algorithm. You cannot use this value to verify that this is the remote host's actual certificate because the NWA has signed the certificate; thus causing this value to be different from that of the remote host's actual certificate. See Section 18.1.2 on page 222 for how to verify a remote host's certificate before you import it into the NWA. Certificate in PEM This read-only text box displays the certificate or certification request (Base-64) in Privacy Enhanced Mail (PEM) format. PEM uses 64 ASCII characters Encoded Format to convert the binary certificate into a printable form. Export Apply Cancel You can copy and paste the certificate into an e-mail to send to friends or colleagues or you can copy and paste the certificate into a text editor and save the file on a management computer for later distribution (via floppy disk for example). Click this button and then Save in the File Download screen. The Save As screen opens, browse to the location that you want to use and click Save. Click Apply to save your changes. You can only change the name and/or set whether or not you want the NWA to check the CRL that the certification authority issues before trusting a certificate issued by the certification authority. Click Cancel to quit and return to the Trusted CAs screen. 236 NWA-3160 Series User's Guide