ZyXEL NWA-3163 User Guide - Page 68
Testing the Configuration
 |
View all ZyXEL NWA-3163 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 68 highlights
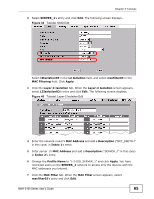
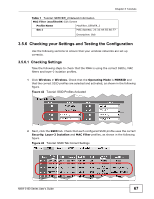
Chapter 3 Tutorials If the settings are not as shown, follow the steps in the relevant section of this tutorial again. 3.5.6.2 Testing the Configuration Before you allow employees to use the network, you need to thoroughly test whether the setup behaves as it should. Take the following steps to do this. 1 Test the SERVER_1 network. • Using Alice's computer and wireless client, and the correct security settings, do the following. Attempt to access Server 1. You should be able to do so. Attempt to access the Internet. You should be able to do so. Attempt to access Server 2. You should be unable to do so. If you can do so, layer-2 isolation is misconfigured. • Using Alice's computer and wireless client, and incorrect security settings, attempt to associate with the SERVER_1 network. You should be unable to do so. If you can do so, security is misconfigured. • Using another computer and wireless client, but with the correct security settings, attempt to associate with the SERVER_1 network. You should be unable to do so. If you can do so, MAC filtering is misconfigured. 2 Test the SERVER_2 network. • Using Bob's computer and wireless client, and the correct security settings, do the following. Attempt to access Server 2. You should be able to do so. Attempt to access the Internet. You should be able to do so. Attempt to access Server 1. You should be unable to do so. If you can do so, layer-2 isolation is misconfigured. • Using Bob's computer and wireless client, and incorrect security settings, attempt to associate with the SERVER_2 network. You should be unable to do so. If you can do so, security is misconfigured. • Using another computer and wireless client, but with the correct security settings, attempt to associate with the SERVER_2 network. You should be unable to do so. If you can do so, MAC filtering is misconfigured. If you cannot do something that you should be able to do, check the settings as described in Section 3.5.6.1 on page 67, and in the individual Security, layer-2 isolation and MAC filter profiles for the relevant network. If this does not help, see the Troubleshooting chapter in this User's Guide. 68 NWA-3160 Series User's Guide