D-Link DGS-3426 User Manual - Page 235
Authentication Server Host, Authentication Server Group Table Add Settings window
 |
View all D-Link DGS-3426 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 235 highlights
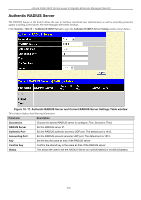
xStack DGS-3400 Series Layer 2 Gigabit Ethernet Managed Switch To add an Authentication Server Host to the list, enter its IP address in the IP Address field, choose the protocol associated with the IP address of the Authentication Server Host and click Add to add this Authentication Server Host to the group. To add a server group other than the ones listed, click the add button, revealing the following window to configure. Figure 10- 23. Authentication Server Group Table Add Settings window Enter a group name of up to 15 characters into the Group Name field and click Apply. The entry should appear in the Authentication Server Group Settings window. NOTE: The user must configure Authentication Server Hosts using the Authentication Server Hosts window before adding hosts to the list. Authentication Server Hosts must be configured for their specific protocol on a remote centralized server before this function can work properly. NOTE: The three built in server groups can only have server hosts running the same TACACS daemon. TACACS/XTACACS/TACACS+ protocols are separate entities and are not compatible with each other. Authentication Server Host This window will set user-defined Authentication Server Hosts for the TACACS / XTACACS / TACACS+ / RADIUS security protocols on the Switch. When a user attempts to access the Switch with Authentication Policy enabled, the Switch will send authentication packets to a remote TACACS / XTACACS / TACACS+ / RADIUS server host on a remote host. The TACACS / XTACACS / TACACS+ / RADIUS server host will then verify or deny the request and return the appropriate message to the Switch. More than one authentication protocol can be run on the same physical server host but, remember that TACACS / XTACACS / TACACS+ / RADIUS are separate entities and are not compatible with each other. The maximum supported number of server hosts is 16. To view the following window, click Security > Access Authentication Control > Authentication Server Host: Figure 10- 24. Authentication Server Host window To add an Authentication Server Host, click the Add button, revealing the following window: 221