Dell PowerEdge M520 Dell PowerConnect M6220/M6348/M8024 Switches Configuration - Page 114
Example #1: Basic RADIUS Server Configuration, secret1
 |
View all Dell PowerEdge M520 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 114 highlights
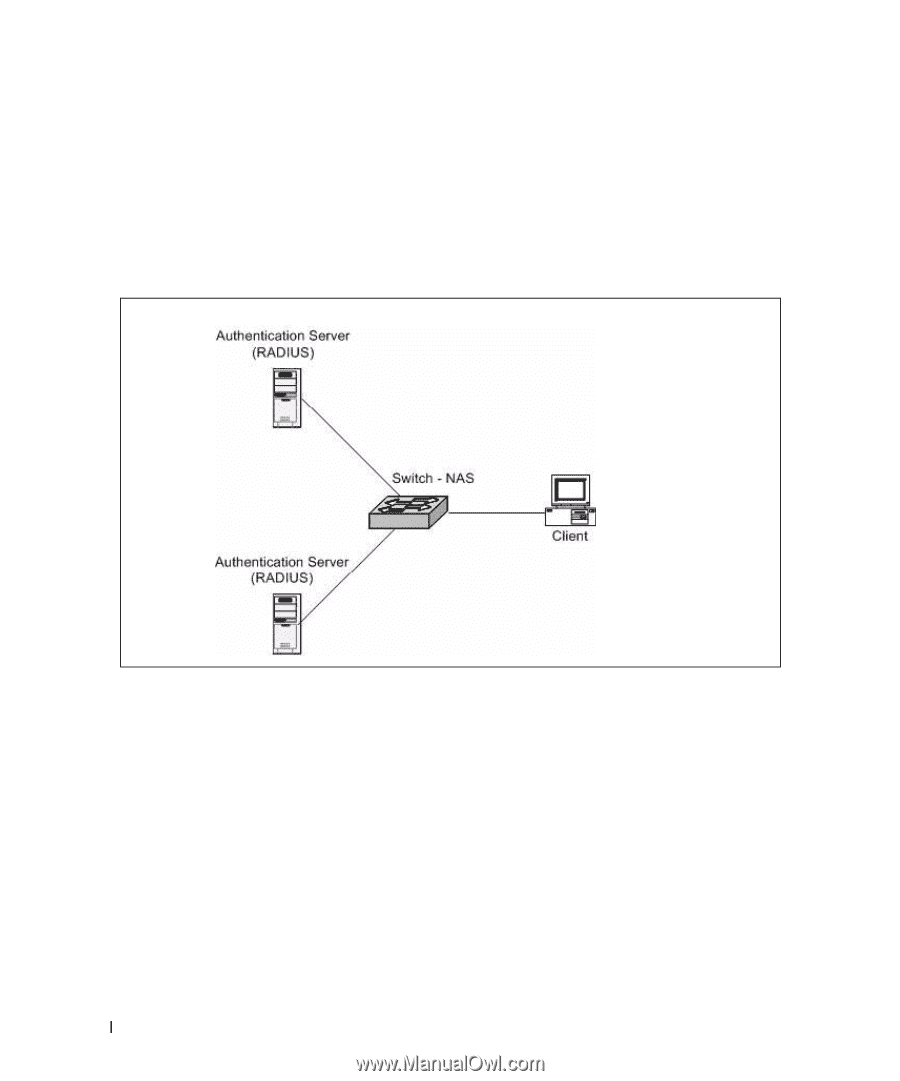
Example #1: Basic RADIUS Server Configuration This example configures two RADIUS servers at 10.10.10.10 and 11.11.11.11. Each server has a unique shared secret key. The shared secrets are configured to be secret1 and secret2 respectively. The server at 10.10.10.10 is configured as the primary server. The process creates a new authentication list, called radiusList, which uses RADIUS as the primary authentication method, and local authentication as a backup method in the event that the RADIUS server cannot be contacted. Figure 5-4. RADIUS Servers in a Network When a user attempts to log in, the switch prompts for a username and password. The switch then attempts to communicate with the primary RADIUS server at 10.10.10.10. Upon successful connection with the server, the login credentials are exchanged over an encrypted channel. The server grants or denies access, which the switch honors, and either allows or does not allow the user to access the switch. If neither of the two servers can be contacted, the switch searches its local user database for the user. console(config)#radius-server host 10.10.10.10 console(Config-radius)#key secret1 console(Config-radius)#priority 1 console(Config-radius)#exit console(config)#radius-server host 11.11.11.11 console(Config-radius)#key secret2 console(Config-radius)#priority 50 console(Config-radius)#exit console(config)#aaa authentication login radiusList radius local 114 Device Security