Dell PowerEdge M520 Dell PowerConnect M6220/M6348/M8024 Switches Configuration - Page 119
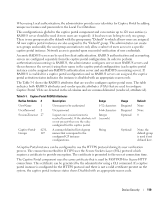
Table 5-1., Captive Portal RADIUS Attributes, Radius Attribute, Description, Range, Usage, Default
 |
View all Dell PowerEdge M520 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 119 highlights
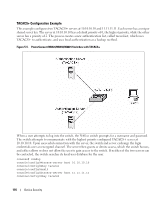
When using Local authentication, the administrator provides user identities for Captive Portal by adding unique user names and passwords to the Local User Database. This configuration is global to the captive portal component and can contain up to 128 user entries (a RADIUS server should be used if more users are required). A local user can belong to only one group. There is one group created by default with the group name "Default" to which all new users are assigned. All new captive portal instances are also assigned to the "Default" group. The administrator can create new groups and modify the user/group association to only allow a subset of users access to a specific captive portal instance. Network access is granted upon successful verification of user credentials. A remote RADIUS server can be used for client authentication. RADIUS authentication and accounting servers are configured separately from the captive portal configuration. In order to perform authentication/accounting via RADIUS, the administrator configures one or more RADIUS servers and then references the server(s) using their name in the captive portal configuration (each captive portal instance can be assigned one RADIUS authentication server and one RADIUS accounting server). If RADIUS is enabled for a captive portal configuration and no RADIUS servers are assigned, the captive portal activation status indicates the instance is disabled with an appropriate reason code. The Table 5-1 shows the RADIUS attributes that are used to configure captive portal users. The table indicates both RADIUS attributes and vendor specific attributes (VSA) that are used to configure Captive Portal. VSAs are denoted in the id column and are comma delimited (vendor id, attribute id). Table 5-1. Captive Portal RADIUS Attributes Radius Attribute # Description User-Name 1 User name to be authorized User-Password 2 User password Session-Timeout 27 Logout once session timeout is reached (seconds). If the attribute is 0 or not present then use the value configured for the captive portal. Captive-Portal- 6231, Groups 127 A comma-delimited list of group names that correspond to the configured CP instance configurations. Range 1-32 characters 8-64 characters Integer (seconds) String Usage Required Required Optional Optional Default None None 0 None; the default group is used if not defined here. A Captive Portal instance can be configured to use the HTTPS protocol during its user verification process. The connection method for HTTPS uses the Secure Sockets Layer (SSL) protocol which requires a certificate to provide encryption. The certificate is presented to the user at connection time. The Captive Portal component uses the same certificate that is used by FASTPATH for Secure HTTP connections. This certificate can be generated by the administrator using a CLI command. If a captive portal instance is configured for the HTTPS protocol and there is not a valid certificate present on the system, the captive portal instance status shows Disabled with an appropriate reason code. Device Security 119