D-Link DFL-260 Product Manual - Page 343
SAT, 7.4.1. Translation of a Single IP Address (1:1), Note: Port forwarding
 |
UPC - 790069296802
View all D-Link DFL-260 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 343 highlights
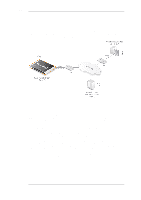
7.4. SAT Chapter 7. Address Translation 7.4. SAT NetDefendOS can translate entire ranges of IP addresses and/or ports. Such translations are transpositions, each address or port is mapped to a corresponding address or port in the new range, rather than translating them all to the same address or port. In NetDefendOS this functionality is known as Static Address Translation (SAT). Note: Port forwarding Some network equipment vendors use the term "port forwarding" when referring to SAT. Both terms are referring to the same functionality. SAT Requires Multiple IP Rules Unlike NAT, SAT requires more than just a single IP rule to be defined. A SAT rule must first be added to specify the address translation but NetDefendOS does not terminate the rule set lookup upon finding a matching SAT rule. Instead, it continues to search for a matching Allow, NAT or FwdFast rule. Only when it has found such a matching rule does NetDefendOS execute the original SAT rule. The SAT rule only defines the translation that is to take place. A second, associated rule, such as an Allow rule, must exist to actually allow the traffic to pass through the firewall. The Second Rule Must Trigger on the Untranslated Destination IP An important principle to keep in mind when creating the IP rules for SAT is that the second rule, for example an Allow rule, must trigger on the untranslated destination IP address. A common mistake is to create a rule which triggers on the translated address given by the SAT rule. For example, if a SAT rule translates the destination from 1.1.1.1 to 2.2.2.2 then the second associated rule should allow traffic to pass to the destination 1.1.1.1 and not 2.2.2.2. Only after the second rule triggers to allow the traffic, is the route lookup then done by NetDefendOS on the translated address to work out which interface the packets should be sent from. 7.4.1. Translation of a Single IP Address (1:1) The simplest form of SAT usage is translation of a single IP address. A very common scenario for this is to enable external users to access a protected server in a DMZ that has a private address. This scenario is also sometimes referred to as a Virtual IP or Virtual Server in some other manufacturer's products. The Role of the DMZ At this point in the manual, it's relevant to discuss the concept and role of the network known as the Demilitarized Zone (DMZ). The DMZ's purpose is to have a network where the administrator can place those resources which will be accessed by external, untrusted clients and typically this access takes place across the public Internet. These servers will have the maximum exposure to external threats and therefore at most risk of being compromised. By isolating these servers in the DMZ, we are creating a distinct separation from the more sensitive local, internal networks. This allows NetDefendOS to better control what traffic flows between the DMZ and internal networks and to better isolate any security breaches that might occur in DMZ servers. 343