D-Link DFL-260 Product Manual - Page 388
L2TP Roaming Clients with Certificates, Enable Proxy ARP on
 |
UPC - 790069296802
View all D-Link DFL-260 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 388 highlights
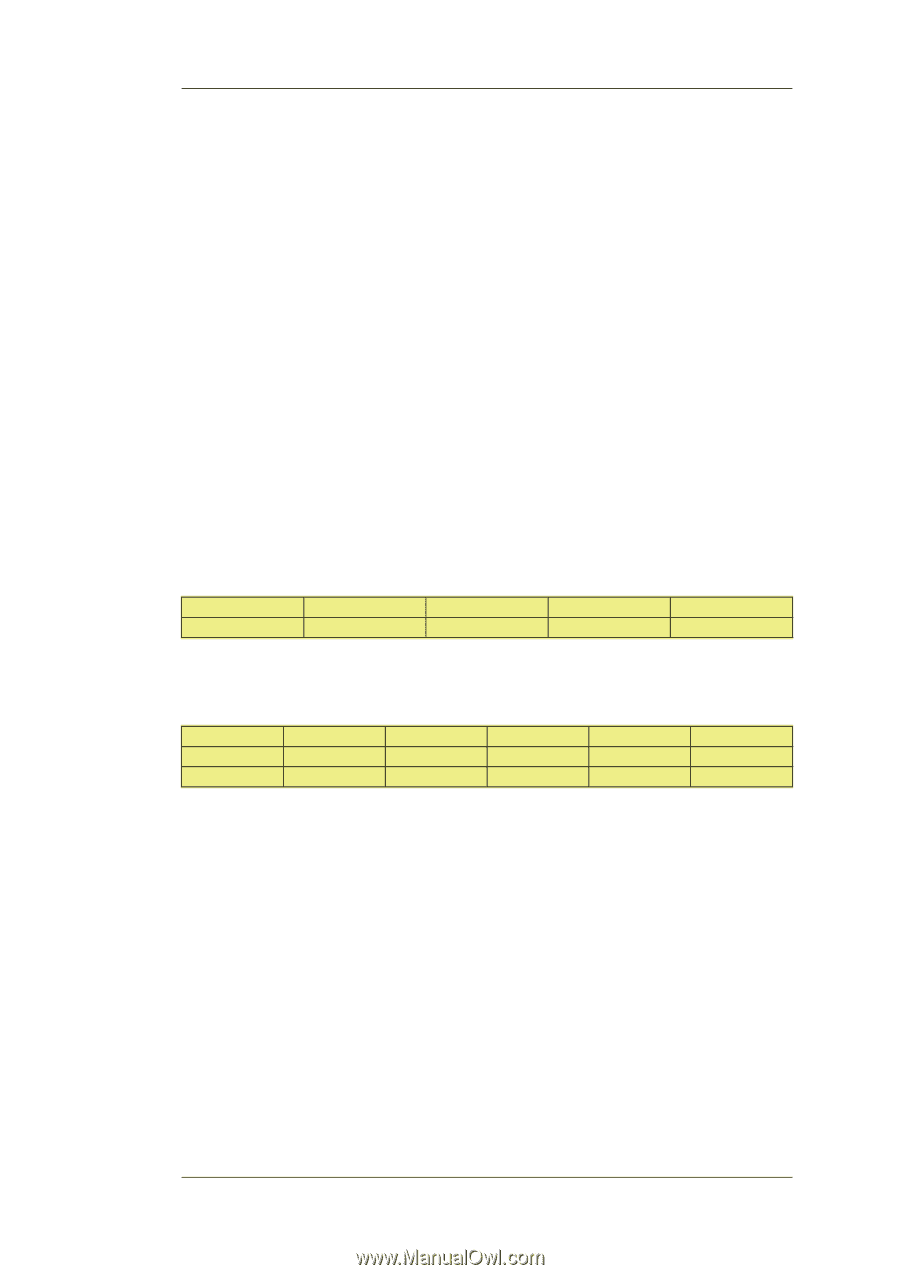
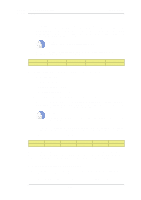
9.2.6. L2TP Roaming Clients with Certificates Chapter 9. VPN • Set Tunnel Protocol to L2TP. • Set Outer Interface Filter to ipsec_tunnel. • Set Outer Server IP to ip_ext. • Select the Microsoft Point-to-Point Encryption allowed. Since IPsec encryption is used this can be set to be None only, otherwise double encryption will degrade throughput. • Set IP Pool to l2tp_pool. • Enable Proxy ARP on the int interface to which the internal network is connected. • Make the interface a member of a specific routing table so that routes are automatically added to that table. Normally the main table is selected. 6. For user authentication: • Define a Local User DB object (let's call this object TrustedUsers). • Add individual users to TrustedUsers. This should consist of at least a username and password combination. The Group string for a user can also be specified. This is explained in the same step in the IPsec Roaming Clients section above. • Define a User Authentication Rule: Agent PPP Auth Source Local Src Network all-nets Interface l2tp_tunnel Client Source IP all-nets (0.0.0.0/0) 7. To allow traffic through the L2TP tunnel the following rules should be defined in the IP rule set: Action Allow NAT Src Interface l2tp_tunnel ipsec_tunnel Src Network l2tp_pool l2tp_pool Dest Interface any ext Dest Network int_net all-nets Service All All The second rule would be included to allow clients to surf the Internet via the ext interface on the NetDefend Firewall. The client will be allocated a private internal IP address which must be NATed if connections are then made out to the public Internet via the NetDefend Firewall. 8. Set up the client. Assuming Windows XP, the Create new connection option in Network Connections should be selected to start the New Connection Wizard. The key information to enter in this wizard is: the resolvable URL of the NetDefend Firewall or alternatively its ip_ext IP address. Then choose Network > Properties. In the dialog that opens choose the L2TP Tunnel and select Properties. In the new dialog that opens select the Networking tab and choose Force to L2TP. Now go back to the L2TP Tunnel properties, select the Security tab and click on the IPsec Settings button. Now enter the pre-shared key. 9.2.6. L2TP Roaming Clients with Certificates If certificates are used with L2TP roaming clients instead of pre-shared keys then the differences in the setup described above are: 388