Netgear FVS338 FVS338 Reference Manual - Page 138
Enabling Remote Management Access, for the procedure on how to do this.
 |
UPC - 606449037197
View all Netgear FVS338 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 138 highlights
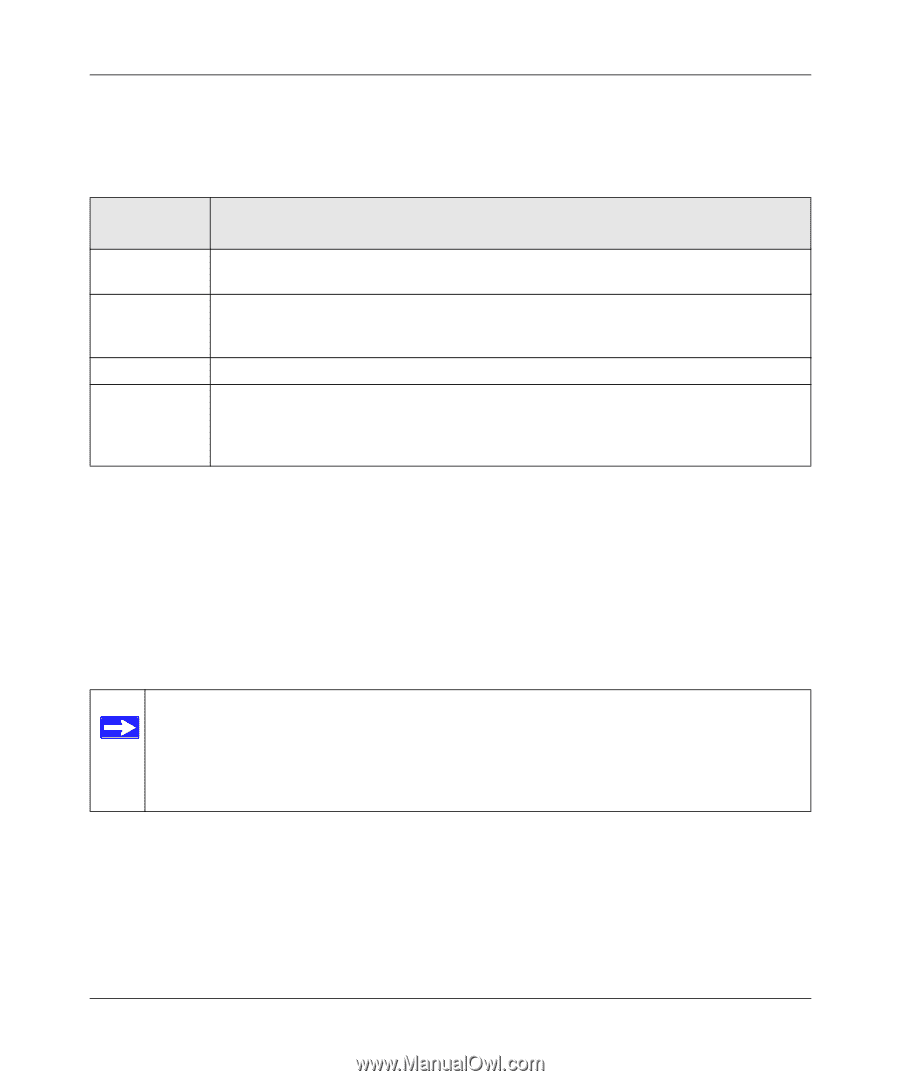
FVS338 ProSafe VPN Firewall 50 Reference Manual When specifying RADIUS domain authentication, you are presented with several authentication protocol choices, as summarized in the following table: Table 6-1. Authentication Protocol Description PAP CHAP MIAS WiKID Password Authentication Protocol (PAP) is a simple protocol in which the client sends a password in clear text. Challenge Handshake Authentication Protocol (CHAP) executes a three-way handshake in which the client and server trade challenge messages, each responding with a hash of the other's challenge message that is calculated using a shared secret value. Network validated PAP or CHAP password based authentication scheme. WiKID is a PAP or CHAP key-based two-factor authentication method using public key cryptography. The client sends an encrypted PIN to the WiKID server and receives a onetime passcode with a short expiration period. The client logs in with the passcode. See Appendix D, "Two Factor Authentication" for more on WiKID authentication. The chosen authentication protocol must be configured on the RADIUS server and on the authenticating client devices. Enabling Remote Management Access Using the Remote Management page, you can allow an administrator on the Internet to configure, upgrade, and check the status of your VPN firewall. You must be logged in locally to enable remote management (see "Logging in to the VPN Firewall" on page 2-1). Note: Be sure to change the firewall default configuration password to a very secure password. The ideal password should contain no dictionary words from any language, and should be a mixture of letters (both upper and lower case), numbers, and symbols. Your password can be up to 30 characters. See "Changing Passwords and Settings" on page 6-7 for the procedure on how to do this. 6-10 v1.0, March 2009 Router and Network Management