Netgear FVS338 FVS338 Reference Manual - Page 58
Inbound Rules Port Forwarding., Dyamic DNS, LAN Groups
 |
UPC - 606449037197
View all Netgear FVS338 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 58 highlights
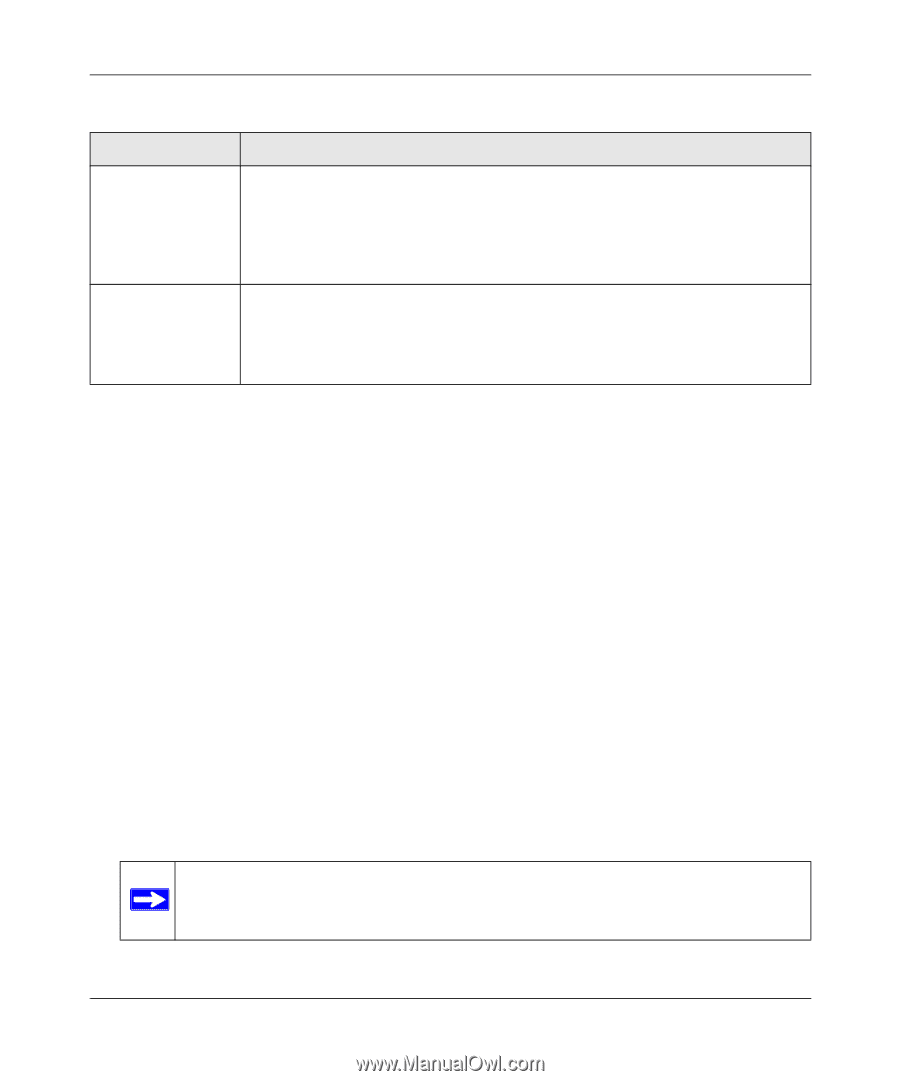
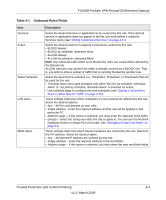
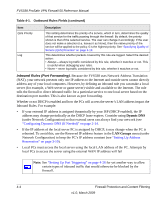
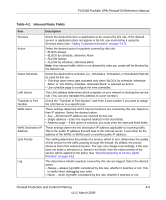
FVS338 ProSafe VPN Firewall 50 Reference Manual Table 4-1. Outbound Rules Fields (continued) Item QoS Priority Log Description This setting determines the priority of a service, which in turn, determines the quality of that service for the traffic passing through the firewall. By default, the priority shown is that of the selected service. The user can change it accordingly. If the user does not make a selection (i.e, leaves it as None), then the native priority of the service will be applied to the policy. 6 is the highest priority. See "Specifying Quality of Service (QoS) Priorities" on page 4-19. This determines whether packets covered by this rule are logged. Select the desired action: • Always - always log traffic considered by this rule, whether it matches or not. This is useful when debugging your rules. • Never - never log traffic considered by this rule, whether it matches or not. Inbound Rules (Port Forwarding). Because the FVS338 uses Network Address Translation (NAT), your network presents only one IP address to the Internet and outside users cannot directly address any of your local computers. However, by defining an inbound rule you can make a local server (for example, a Web server or game server) visible and available to the Internet. The rule tells the firewall to direct inbound traffic for a particular service to one local server based on the destination port number. This is also known as port forwarding. Whether or not DHCP is enabled and how the PCs will access the server's LAN address impact the Inbound Rules. For example: • If your external IP address is assigned dynamically by your ISP (DHCP enabled), the IP address may change periodically as the DHCP lease expires. Consider using Dyamic DNS (under Network Configuration) so that external users can always find your network (see "Configuring Dynamic DNS (If Needed)" on page 2-14. • If the IP address of the local server PC is assigned by DHCP, it may change when the PC is rebooted. To avoid this, use the Reserved IP address feature in the LAN Groups menu (under Network Configuration) to keep the PC's IP address constant (see "Setting Up Address Reservation" on page 3-10). • Local PCs must access the local server using the local LAN address of the PC. Attempts by local PCs to access the server using the external WAN IP address will fail . Note: See "Setting Up Port Triggering" on page 4-26 for yet another way to allow certain types of inbound traffic that would otherwise be blocked by the firewall. 4-4 Firewall Protection and Content Filtering v1.0, March 2009