Kyocera FS-6525MFP Fax System (U) Operation Guide Rev-4.2012.3 - Page 124
Encryption, Registering an Encryption Key
 |
View all Kyocera FS-6525MFP manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 124 highlights
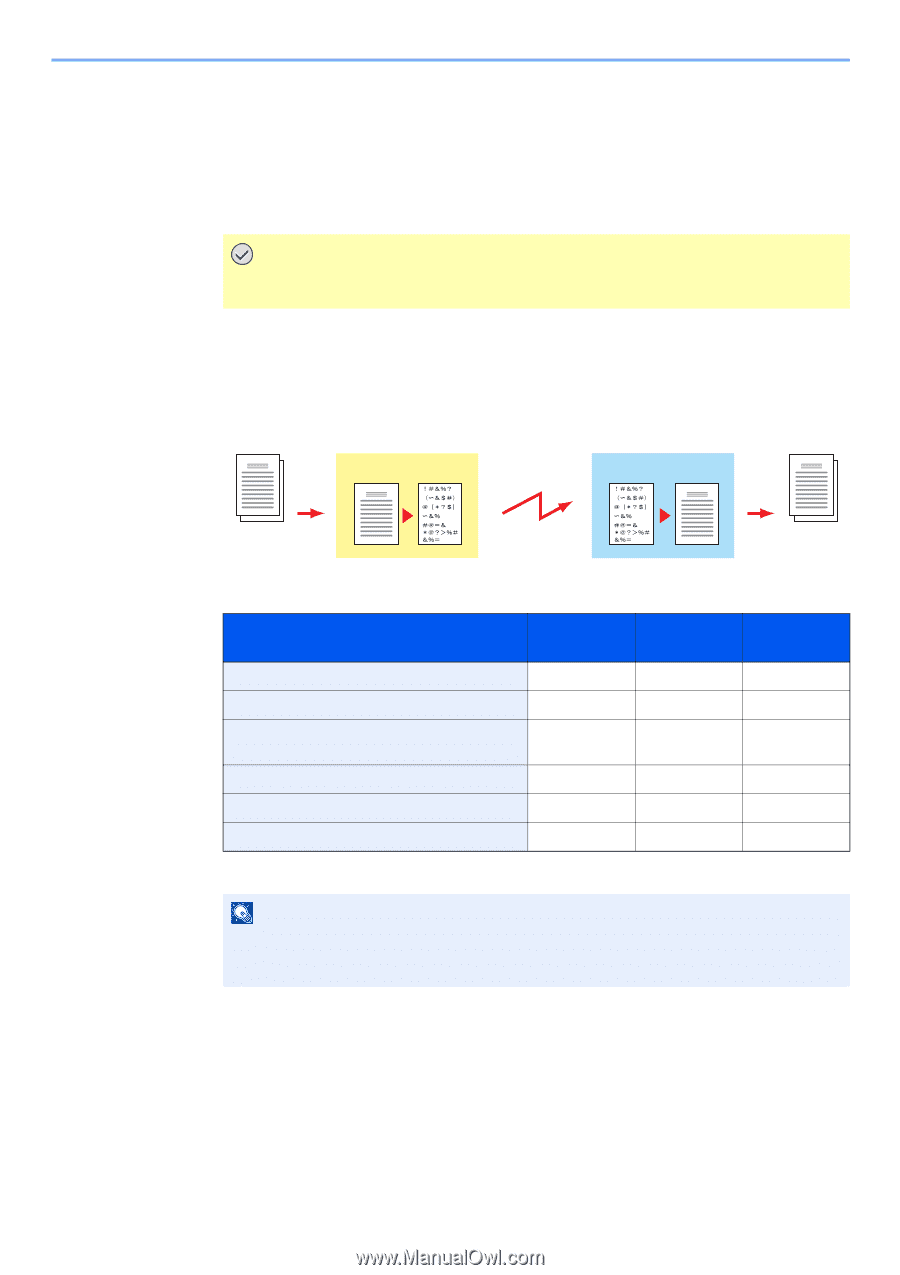
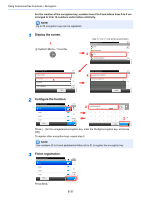
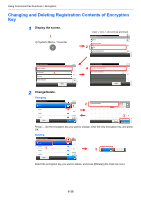
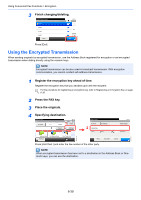
Using Convenient Fax Functions > Encryption Encryption This method allows you to communicate with originals encrypted by the sending system. Therefore, even when a third party tries to view the originals in the middle of communication by some means, the third party is prevented from knowing the actual contents of the originals. The originals received are reverted to the originals as they were before transmission (decrypted) by the receiving system, and printed. This is an extremely effective communication method for sending confidential documents that are not to be opened by a third party. IMPORTANT In order to use encryption communication, the fax of the other party needs to be an our-brand system with the same type of encryption functions. In encryption communication, in order to encrypt and decrypt originals, the sending and receiving systems must use the same 16-digit encryption key. When the encryption key differs between the sending system and the receiving system, the encryption cannot be conducted. Therefore, the sending system and the receiving system need to have the same encryption key and 2-digit key No. registered in advance. Sending system Receiving system Encrypt Decrypt Scan originals Encryption Output originals Description of settings at sending and receiving systems Settings Sending system Receiving system Encryption Key No. (A) 2 digits (B) 2 digits Encryption Key (C) 16 digits (C) 16 digits Key No. of Address Book (or when the number (A) 2 digits ― is directly dialed) Receiving system encryption box number* (D) 4 digits ― Encryption Box No.* ― (D) 4 digits Key No. in reception setting ― (B) 2 digits Reference page 6-36 6-36 6-39 6-39 ― 6-42 * When the machine receives originals, the Encryption Box is not used. NOTE Set the same characters for the numbers indicated by the same letter in parentheses. For example, the same characters should be used as the encryption key (C) in both the sending and receiving systems. Registering an Encryption Key An encryption key is required when registering the Address Book used for encryption communication (the other party is directly entered using the numeric keys) in the sending system and when setting encryption in the receiving system. 6-36