Dell PowerConnect 8100 Release Notes - Page 71
Layer 2 - 4.2.0.4
 |
View all Dell PowerConnect 8100 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 71 highlights
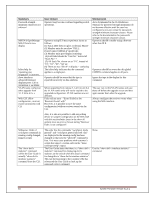
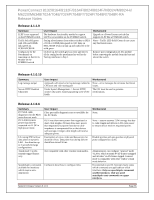
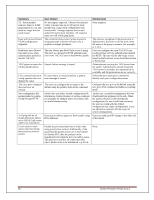
PowerConnect 8132/8164/8132F/8164F/8024/8024F/M8024/M8024-k/ M6220/M6348/7024/7048/7024P/7048P/7024F/7048R/7048R-RA Release Notes MjMO+BPP5KXzNWfZhqAhxBSoBvif/z6pzi9xWLlYy99A03zmRYCpcGIoLW iRHsR7NVpxFqwbqvez8KS0CDJ5aoKKLrpBlpg5ETkYEew/uTZ14lQQRBrzPw GBfxvTXKCWiI2j5KFa/WKLSnmWJX0/98qpxW/lMXoXsA9iK4pnMKwAAAI B4Jrt6jmoLybpzgOPOI0DsJ7jQwWacinD0jliz8k+qzCpanhd2wH+DEdj/xO2sFR fnYlME3hmXoB+7NByVUtheVjuQ2CWhcGFIKm9tbuPC6DtXh1xxT0NJ7rspv Lgb0s6y/0tk+94ZP5RCoAtLZ7wirShy3/KJ4RE0y2SFZjIVjQ==" console(config-pubkey-key)#exit console(config-pubkey-chain)#exit console(config)#exit console#show crypto key pubkey-chain ssh username asd Username : asd ssh-dss AAAAB3NzaC1kc3MAAACBAJRwUAD3AuRACp1MObBeh1AgyZb18wf9Bt dip+t+1CbAqiqNEh4lBiew184DSKk0T6SnSSXuCN+bJnQPxJeiQt+OFnmjiYhn HcvI04Q5KnQhloZcEFgSsmQ7zJnReWtLvUQI0QvBIStanzedmQVGHvDrQ5X 2R729ToSH0ibBrnYtAAAAFQDNord7S9EJvUkKKxVBpWE6/skCmQAAAIB MjMO+BPP5KXzNWfZhqAhxBSoBvif/z6pzi9xWLlYy99A03zmRYCpcGIoLW iRHsR7NVpxFqwbqvez8KS0CDJ5aoKKLrpBlpg5ETkYEew/uTZ14lQQRBrzPw GBfxvTXKCWiI2j5KFa/WKLSnmWJX0/98qpxW/lMXoXsA9iK4pnMKwAAAI B4Jrt6jmoLybpzgOPOI0DsJ7jQwWacinD0jliz8k+qzCpanhd2wH+DEdj/xO2sFR fnYlME3hmXoB+7NByVUtheVjuQ2CWhcGFIKm9tbuPC6DtXh1xxT0NJ7rspv Lgb0s6y/0tk+94ZP5RCoAtLZ7wirShy3/KJ4RE0y2SFZjIVjQ== Fingerprint : d9:d1:21:ad:26:41:ba:43:b1:dc:5c:6c:b9:57:07:6c Broadcom NIC link always stays up within the m8024-k status even after disabling server port through device manager or turning off server altogether. SSH RSA or DSA keys can be generated by using the ssh-keygen command on a Unix system or with other publicly available utilities. Low- This is works as designed and is necessary for new features for 12G. The Broadcom NIC 57810S never reports to the internal switch that the link is down because it needs the link to be up so that internal communications can continue with iDRAC and for other various components even after disabling the link on the server side. Release 4.2.0.4 Layer 2 - 4.2.0.4 802.1x Authentication Description Windows Vista® Authentication - The Windows Vista® client could fail to authenticate properly when the option to cache user credentials is selected. The maximum number of 802.1x clients per port is 4. The maximum number of configurable traffic classes is 7. User Impact Low Workaround: 1. In Control Panel Network Connections, right-click on the desired Local Area Connection and select Properties. 2. In the Properties window, select the Authentication tab. 3. Deselect the checkbox for Cache user information for subsequent connections to this network. 4. Click OK. Low - most deployments will have at most 2 802.1x clients per physical port. Note: If running Release 5.1.0.1 or later version of firmware, the maximum number is 24. Low as most deployments use a single traffic class. Some limited deployments may use up to 3 traffic classes. System Firmware Version 5.1.0.1 Page 69