ZyXEL MAX-306 User Guide - Page 234
Table 97, Access Control Logs, TCP Reset Logs, System Maintenance Logs continued
 |
View all ZyXEL MAX-306 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 234 highlights
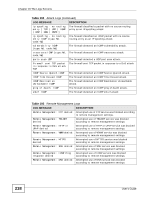
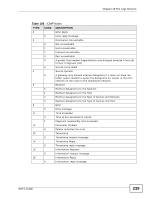
Chapter 19 The Logs Screens Table 96 System Maintenance Logs (continued) LOG MESSAGE DESCRIPTION Connect to NTP server fail The device was not able to connect to the NTP server. Too large ICMP packet has been dropped The device dropped an ICMP packet that was too large. Configuration Change: PC = 0x%x, Task ID = 0x%x The device is saving configuration changes. Table 97 Access Control Logs LOG MESSAGE Firewall default policy: [ TCP | UDP | IGMP | ESP | GRE | OSPF ] Firewall rule [NOT] match:[ TCP | UDP | IGMP | ESP | GRE | OSPF ] , Triangle route packet forwarded: [ TCP | UDP | IGMP | ESP | GRE | OSPF ] Packet without a NAT table entry blocked: [ TCP | UDP | IGMP | ESP | GRE | OSPF ] Router sent blocked web site message: TCP Exceed maximum sessions per host (%d). Firewall allowed a packet that matched a NAT session: [ TCP | UDP ] DESCRIPTION Attempted TCP/UDP/IGMP/ESP/GRE/OSPF access matched the default policy and was blocked or forwarded according to the default policy's setting. Attempted TCP/UDP/IGMP/ESP/GRE/OSPF access matched (or did not match) a configured firewall rule (denoted by its number) and was blocked or forwarded according to the rule. The firewall allowed a triangle route session to pass through. The router blocked a packet that didn't have a corresponding NAT table entry. The router sent a message to notify a user that the router blocked access to a web site that the user requested. The device blocked a session because the host's connections exceeded the maximum sessions per host. A packet from the WAN (TCP or UDP) matched a cone NAT session and the device forwarded it to the LAN. 234 Table 98 TCP Reset Logs LOG MESSAGE Under SYN flood attack, sent TCP RST Exceed TCP MAX incomplete, sent TCP RST Peer TCP state out of order, sent TCP RST DESCRIPTION The router sent a TCP reset packet when a host was under a SYN flood attack (the TCP incomplete count is per destination host.) The router sent a TCP reset packet when the number of TCP incomplete connections exceeded the user configured threshold. (the TCP incomplete count is per destination host.) The router sent a TCP reset packet when a TCP connection state was out of order.Note: The firewall refers to RFC793 Figure 6 to check the TCP state. User's Guide