ZyXEL MAX-306 User Guide - Page 237
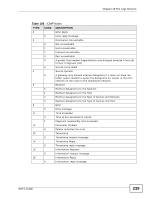
Table 104, Attack Logs, Content Filtering Logs continued
 |
View all ZyXEL MAX-306 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 237 highlights
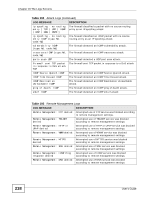
Chapter 19 The Logs Screens Table 103 Content Filtering Logs (continued) LOG MESSAGE DESCRIPTION %s: Trusted Web site The web site is in a trusted domain. %s When the content filter is not on according to the time schedule: Waiting content filter server timeout The external content filtering server did not respond within the timeout period. DNS resolving failed The WiMAX Device cannot get the IP address of the external content filtering via DNS query. Creating socket failed The WiMAX Device cannot issue a query because TCP/UDP socket creation failed, port:port number. Connecting to content filter server fail The connection to the external content filtering server failed. License key is invalid The external content filtering license key is invalid. For type and code details, see Table 106 on page 239. Table 104 Attack Logs LOG MESSAGE attack [ TCP | UDP | IGMP | ESP | GRE | OSPF ] attack ICMP (type:%d, code:%d) land [ TCP | UDP | IGMP | ESP | GRE | OSPF ] land ICMP (type:%d, code:%d) ip spoofing - WAN [ TCP | UDP | IGMP | ESP | GRE | OSPF ] ip spoofing - WAN ICMP (type:%d, code:%d) icmp echo : ICMP (type:%d, code:%d) syn flood TCP ports scan TCP teardrop TCP teardrop UDP teardrop ICMP (type:%d, code:%d) illegal command TCP NetBIOS TCP DESCRIPTION The firewall detected a TCP/UDP/IGMP/ESP/GRE/OSPF attack. The firewall detected an ICMP attack. The firewall detected a TCP/UDP/IGMP/ESP/GRE/OSPF land attack. The firewall detected an ICMP land attack. The firewall detected an IP spoofing attack on the WAN port. The firewall detected an ICMP IP spoofing attack on the WAN port. The firewall detected an ICMP echo attack. The firewall detected a TCP syn flood attack. The firewall detected a TCP port scan attack. The firewall detected a TCP teardrop attack. The firewall detected an UDP teardrop attack. The firewall detected an ICMP teardrop attack. The firewall detected a TCP illegal command attack. The firewall detected a TCP NetBIOS attack. User's Guide 237